Hopf fibration
Free Action
The orbit of an element x in X is the set of elements in X to which x can be moved by the elements of G. The orbit of x is denoted by G⋅x: The defining properties of a group guarantee that the set of orbits of (points x in) X under the action of G form a partition of X.A group action
The basic example of a free group action is the action of a group on itself by left multiplication
Complex number
nth root
Semigroup action
Radian
Ribbon theory
Category
theory formalizes mathematical structure and its concepts in terms of a
labeled directed graph called a category, whose nodes are called
objects, and whose labelled directed edges are called arrows
Saint Hubertus or Hubert
( c. 656 – 30 May 727) was a Christian saint who became the first
bishop of Liège in 708 AD. He was the patron saint of hunters,
mathematicians, opticians, and metalworkers.
Repeating experiments has major uses:
- Repetition reduces the likelihood of errors or anomalous results (verification)
- Scientists repeat others' experiments to verify the accuracy of the findings (peer review)
- Repeating an experiment allows a person to refine the results or simplify the methodology.
Pigeons' discrimination of paintings by Monet and Picasso
Pigeonhole principle in discrete mathematics
Pakistani villager urges India to return 'spy' pigeon
Fat cat is a political term originally describing a rich political donor, also called an angel or big money man.
throw the cat among the pigeons
To do or say something that is likely to cause alarm, controversy, or unrest among a lot of people.
(data) slice and dice
To slice and dice is to break a body of information down into smaller
parts or to examine it from different viewpoints so that you can
understand it better.
The term has its roots in cooking and describes two types of knife
skills every chef needs to master. To slice means to cut and to dice
means to cut into very small uniform sections and the two actions are
often performed sequentially. For example, a chef may first cut an onion
into slices and then cut the slices up into dices. In data analysis,
the term generally implies a systematic reduction of a body of data into
smaller parts or views that will yield more information. The term is
also used to mean the presentation of information in a variety of
different and useful ways.
Pivot tables are a popular self-service BI tool for slicing and dicing data. Essentially, a pivot table sorts, counts and totals the data stored in one database table or spreadsheet and creates a second table – the actual pivot table – that summarizes the data. Typically, users will use a pivot table to extract information from a BI solution’s data warehouse in order to mine through data in an interactive manner without requiring the IT department to run an ad hoc report.
Slice and dice contrasts with the terms drill down, drill across and roll up. To drill down is to look at more detailed data in progressively deeper levels of a body of information's hierarchy. To drill across is to compare data in similar levels of a body of information's hierarchy, and to roll up is to aggregate data by removing detail levels from the hierarchy.
Small & Minority Business Resources
In addition, the set of palindromes may not be reliably tested by a deterministic pushdown automaton which also means that they are not LR(k)-parsable or LL(k)-parsable. When reading a palindrome from left-to-right, it is, in essence, impossible to locate the "middle" until the entire word has been read completely.
It is possible to find the longest palindromic substring of a given input string in linear time.
The palindromic density of an infinite word w over an alphabet A is defined to be zero if only finitely many prefixes are palindromes; otherwise, letting the palindromic prefixes be of lengths nk for k=1,2,... we define the density to be
Among aperiodic words, the largest possible palindromic density is achieved by the Fibonacci word, which has density 1/φ, where φ is the Golden ratio.
A palstar is a concatenation of palindromic strings, excluding the trivial one-letter palindromes – otherwise all strings would be palstars.
Bombyx mori, the domestic silk moth, is an insect from the moth family Bombycidae. It is the closest relative of Bombyx mandarina, the wild silk moth. The silkworm is the larva or caterpillar of a silk moth. It is an economically important insect, being a primary producer of silk. A silkworm's preferred food is white mulberry leaves, though they may eat other mulberry species and even Osage orange. Domestic silk moths are closely dependent on humans for reproduction, as a result of millennia of selective breeding. Wild silk moths are different from their domestic cousins as they have not been selectively bred; they are thus not as commercially viable in the production of silk.
They're called crustaceans. Shrimp, crabs, lobsters – they're arthropods, just like crickets. They're also scavengers, which means their diets are as filthy as any bug's.
Commercial chitosan is derived from the shells of shrimp and other sea crustaceans
A node is a point along a standing wave where the wave has minimum amplitude. For instance, in a vibrating guitar string, the ends of the string are nodes. By changing the position of the end node through frets, the guitarist changes the effective length of the vibrating string and thereby the note played. The opposite of a node is an anti-node, a point where the amplitude of the standing wave is at maximum. These occur midway between the nodes
Pivot tables are a popular self-service BI tool for slicing and dicing data. Essentially, a pivot table sorts, counts and totals the data stored in one database table or spreadsheet and creates a second table – the actual pivot table – that summarizes the data. Typically, users will use a pivot table to extract information from a BI solution’s data warehouse in order to mine through data in an interactive manner without requiring the IT department to run an ad hoc report.
Slice and dice contrasts with the terms drill down, drill across and roll up. To drill down is to look at more detailed data in progressively deeper levels of a body of information's hierarchy. To drill across is to compare data in similar levels of a body of information's hierarchy, and to roll up is to aggregate data by removing detail levels from the hierarchy.
Small & Minority Business Resources
City government office in Austin, Texas
Address: 4201 Ed Bluestein Blvd, Austin, TX 78721
Phone: (512) 974-7600
CRISPR (/ˈkrɪspər/)
(clustered regularly interspaced short palindromic repeats) is a family
of DNA sequences found in the genomes of prokaryotic organisms such as
bacteria and archaea. These sequences are derived from DNA fragments of
bacteriophages that had previously infected the prokaryote.
In most genomes or sets of genetic instructions, palindromic motifs are found. The meaning of palindrome in the context of genetics is slightly different, however, from the definition used for words and sentences. Since the DNA is formed by two paired strands of nucleotides, and the nucleotides always pair in the same way (Adenine (A) with Thymine (T), Cytosine (C) with Guanine (G)), a (single-stranded) sequence of DNA is said to be a palindrome if it is equal to its complementary sequence read backward. For example, the sequence ACCTAGGT is palindromic because its complement is TGGATCCA, which is equal to the original sequence in reverse complement.
A palindromic DNA sequence may form a hairpin. Palindromic motifs are made by the order of the nucleotides that specify the complex chemicals (proteins) that, as a result of those genetic instructions, the cell is to produce. They have been specially researched in bacterial chromosomes and in the so-called Bacterial Interspersed Mosaic Elements (BIMEs) scattered over them. Recently a research genome sequencing project discovered that many of the bases on the Y-chromosome are arranged as palindromes. A palindrome structure allows the Y-chromosome to repair itself by bending over at the middle if one side is damaged.
It is believed that palindromes frequently are also found in proteins, but their role in the protein function is not clearly known. It has recently been suggested that the prevalence existence of palindromes in peptides might be related to the prevalence of low-complexity regions in proteins, as palindromes frequently are associated with low-complexity sequences. Their prevalence might also be related to an alpha helical formation propensity of these sequences, or in formation of proteins/protein complexes.
In most genomes or sets of genetic instructions, palindromic motifs are found. The meaning of palindrome in the context of genetics is slightly different, however, from the definition used for words and sentences. Since the DNA is formed by two paired strands of nucleotides, and the nucleotides always pair in the same way (Adenine (A) with Thymine (T), Cytosine (C) with Guanine (G)), a (single-stranded) sequence of DNA is said to be a palindrome if it is equal to its complementary sequence read backward. For example, the sequence ACCTAGGT is palindromic because its complement is TGGATCCA, which is equal to the original sequence in reverse complement.
A palindromic DNA sequence may form a hairpin. Palindromic motifs are made by the order of the nucleotides that specify the complex chemicals (proteins) that, as a result of those genetic instructions, the cell is to produce. They have been specially researched in bacterial chromosomes and in the so-called Bacterial Interspersed Mosaic Elements (BIMEs) scattered over them. Recently a research genome sequencing project discovered that many of the bases on the Y-chromosome are arranged as palindromes. A palindrome structure allows the Y-chromosome to repair itself by bending over at the middle if one side is damaged.
It is believed that palindromes frequently are also found in proteins, but their role in the protein function is not clearly known. It has recently been suggested that the prevalence existence of palindromes in peptides might be related to the prevalence of low-complexity regions in proteins, as palindromes frequently are associated with low-complexity sequences. Their prevalence might also be related to an alpha helical formation propensity of these sequences, or in formation of proteins/protein complexes.
Palindromic sequence
Computation theory
In automata theory, a set of all palindromes in a given alphabet is a typical example of a language that is context-free, but not regular. This means that it is impossible for a computer with a finite amount of memory to reliably test for palindromes. (For practical purposes with modern computers, this limitation would apply only to impractically long letter-sequences.)In addition, the set of palindromes may not be reliably tested by a deterministic pushdown automaton which also means that they are not LR(k)-parsable or LL(k)-parsable. When reading a palindrome from left-to-right, it is, in essence, impossible to locate the "middle" until the entire word has been read completely.
It is possible to find the longest palindromic substring of a given input string in linear time.
The palindromic density of an infinite word w over an alphabet A is defined to be zero if only finitely many prefixes are palindromes; otherwise, letting the palindromic prefixes be of lengths nk for k=1,2,... we define the density to be
Among aperiodic words, the largest possible palindromic density is achieved by the Fibonacci word, which has density 1/φ, where φ is the Golden ratio.
A palstar is a concatenation of palindromic strings, excluding the trivial one-letter palindromes – otherwise all strings would be palstars.
A prokaryote is a unicellular organism that lacks a membrane-bound nucleus, mitochondria, or any other membrane-bound organelle.[1] The word prokaryote comes from the Greek πρό (pro, 'before') and κάρυον (karyon, 'nut' or 'kernel').[2][3] Prokaryotes are divided into two domains, Archaea and Bacteria. Organisms with nuclei and other organelles are placed in a third domain, Eukaryota.[4] Prokaryotes are asexual, reproducing without fusion of gametes. The first organisms are thought to have been prokaryotes.
Horizontal Gene Transfer in Silkworm, Bombyx Mori
Bombyx mori, the domestic silk moth, is an insect from the moth family Bombycidae. It is the closest relative of Bombyx mandarina, the wild silk moth. The silkworm is the larva or caterpillar of a silk moth. It is an economically important insect, being a primary producer of silk. A silkworm's preferred food is white mulberry leaves, though they may eat other mulberry species and even Osage orange. Domestic silk moths are closely dependent on humans for reproduction, as a result of millennia of selective breeding. Wild silk moths are different from their domestic cousins as they have not been selectively bred; they are thus not as commercially viable in the production of silk.
Expression and characterization of cecropinXJ, a bioactive antimicrobial peptide from Bombyx mori (Bombycidae, Lepidoptera) in Escherichia coli
They're called crustaceans. Shrimp, crabs, lobsters – they're arthropods, just like crickets. They're also scavengers, which means their diets are as filthy as any bug's.
Commercial chitosan is derived from the shells of shrimp and other sea crustaceans
Pass the Land Shrimp
By
Chitin nanofibers are extracted from
crustacean waste and mushrooms for possible development of products in
tissue engineering, medicine, and industry.
Cathode and Anode waves
Cathode waves wind the cosmic clock centripetally Anode transverse waves unwind it centrifugally
A node is a point along a standing wave where the wave has minimum amplitude. For instance, in a vibrating guitar string, the ends of the string are nodes. By changing the position of the end node through frets, the guitarist changes the effective length of the vibrating string and thereby the note played. The opposite of a node is an anti-node, a point where the amplitude of the standing wave is at maximum. These occur midway between the nodes
Mathematics
- Vertex (graph theory), a vertex in a mathematical graph
- Node (autonomous system), behaviour for an ordinary differential equation near a critical point
- Singular point of an algebraic variety, a type of singular point of a curve
Physics
- Node (physics), a point along a standing wave where the wave has minimal amplitude
Biology
- Lymph node, an immune system organ used to store white blood cells
- Node of Ranvier, periodic gaps in the insulating myelin sheaths of myelinated axons
- Sinoatrial node and atrioventricular node, specialized tissues in the heart responsible for initiating and coordinating the heartbeat
- Primitive node is the organizer tissue for gastrulation in vertebrates.
- The place on a plant stem where a leaf is attached
- In Cladistics, a shared ancestor (also see Clade)
Mexican silver coins in silky minority business history
By David V. B. Hirsch
Memorylessness
In probability and statistics, memorylessness is a property of certain probability distributions.
It usually refers to the cases when the distribution of a "waiting
time" until a certain event does not depend on how much time has elapsed
already. To model memoryless situations accurately, we must constantly
'forget' which state the system is in: the probabilities would not be
influenced by the history of the process.[1]
Only two kinds of distributions are memoryless: geometric distributions of non-negative integers and the exponential distributions of non-negative real numbers.
In the context of Markov processes, memorylessness refers to the Markov property,[2] an even stronger assumption which implies that the properties of random variables related to the future depend only on relevant information about the current time, not on information from further in the past. The present article describes the use outside the Markov property.
Only two kinds of distributions are memoryless: geometric distributions of non-negative integers and the exponential distributions of non-negative real numbers.
In the context of Markov processes, memorylessness refers to the Markov property,[2] an even stronger assumption which implies that the properties of random variables related to the future depend only on relevant information about the current time, not on information from further in the past. The present article describes the use outside the Markov property.
Waiting time examples
With memory
Most phenomena are not memoryless, which means that observers will obtain information about them over time. For example, suppose that X is a random variable, the lifetime of a car engine, expressed in terms of "number of miles driven until the engine breaks down". It is clear, based on our intuition, that an engine which has already been driven for 300,000 miles will have a much lower X than would a second (equivalent) engine which has only been driven for 1,000 miles. Hence, this random variable would not have the memorylessness property.Without memory
In contrast, let us examine a situation which would exhibit memorylessness. Imagine a long hallway, lined on one wall with thousands of safes. Each safe has a dial with 500 positions, and each has been assigned an opening position at random. Imagine that an eccentric person walks down the hallway, stopping once at each safe to make a single random attempt to open it. In this case, we might define random variable X as the lifetime of their search, expressed in terms of "number of attempts the person must make until they successfully open a safe". In this case, E[X] will always be equal to the value of 500, regardless of how many attempts have already been made. Each new attempt has a (1/500) chance of succeeding, so the person is likely to open exactly one safe sometime in the next 500 attempts – but with each new failure they make no "progress" toward ultimately succeeding. Even if the safe-cracker has just failed 499 consecutive times (or 4,999 times), we expect to wait 500 more attempts until we observe the next success. If, instead, this person focused their attempts on a single safe, and "remembered" their previous attempts to open it, they would be guaranteed to open the safe after, at most, 500 attempts (and, in fact, at onset would only expect to need 250 attempts, not 500).Real-life examples of memorylessness include the universal law of radioactive decay, which describes the time until a given radioactive particle decays, and the time until the discovery of a new Bitcoin block. An often used (theoretical) example of memorylessness in queueing theory is the time a storekeeper must wait before the arrival of the next customer.
The memoryless distribution is an exponential distribution
In probability theory and intertemporal portfolio choice, the Kelly criterion (or strategy, formula, bet, ...), also known as the scientific gambling method, is a formula for bet sizing that leads almost surely
to higher wealth compared to any other strategy in the long run (i.e.
approaching the limit as the number of bets goes to infinity). The Kelly
bet size is found by maximizing the expected value
of the logarithm of wealth, which is equivalent to maximizing the
expected geometric growth rate. The Kelly Criterion is to bet a
predetermined fraction of assets, and it can seem counterintuitive as it
contradicts the St. Petersburg paradox.
It was described by J. L. Kelly, Jr, a researcher at Bell Labs, in 1956.[1] The practical use of the formula has been demonstrated.[2][3][4]
For an even money bet, the Kelly criterion computes the wager size percentage by multiplying the percent chance to win by two, then subtracting one. So, for a bet with a 70% chance to win (or 0.7 probability), doubling 0.7 equates 1.4, from which you subtract 1, leaving 0.4 as your optimal wager size: 40% of available funds. [check the Statement for better clarification]
In recent years, Kelly-style analysis has become a part of mainstream investment theory[5] and the claim has been made that well-known successful investors including Warren Buffett[6] and Bill Gross[7] use Kelly methods. William Poundstone wrote an extensive popular account of the history of Kelly betting.[8]
Kelly formalism is beneficial only in a restricted comparison to alternative formulas for bet sizing. Successful betting formulas are impossible, and ruin is inevitable when betting persistently. A Kelly system may take longer to approach ruin, or exponentially decline to trivial bets, compared to alternative systems.
More specifically, a property holds almost everywhere if it holds for all elements in a set except a subset of measure zero,[1][2][3] or equivalently, if the set of elements for which the property holds is conull. In cases where the measure is not complete, it is sufficient that the set be contained within a set of measure zero. When discussing sets of real numbers, the Lebesgue measure is usually assumed unless otherwise stated.
The term almost everywhere is abbreviated a.e.;[4] in older literature p.p. is used, to stand for the equivalent French language phrase presque partout.[5]
A set with full measure is one whose complement is of measure zero. In probability theory, the terms almost surely, almost certain and almost always refer to events with probability 1 not necessarily including all of the outcomes[1]. These are exactly the sets of full measure in a probability space.
Occasionally, instead of saying that a property holds almost everywhere, it is said that the property holds for almost all elements (though the term almost all can also have other meanings).
It was described by J. L. Kelly, Jr, a researcher at Bell Labs, in 1956.[1] The practical use of the formula has been demonstrated.[2][3][4]
For an even money bet, the Kelly criterion computes the wager size percentage by multiplying the percent chance to win by two, then subtracting one. So, for a bet with a 70% chance to win (or 0.7 probability), doubling 0.7 equates 1.4, from which you subtract 1, leaving 0.4 as your optimal wager size: 40% of available funds. [check the Statement for better clarification]
In recent years, Kelly-style analysis has become a part of mainstream investment theory[5] and the claim has been made that well-known successful investors including Warren Buffett[6] and Bill Gross[7] use Kelly methods. William Poundstone wrote an extensive popular account of the history of Kelly betting.[8]
Kelly formalism is beneficial only in a restricted comparison to alternative formulas for bet sizing. Successful betting formulas are impossible, and ruin is inevitable when betting persistently. A Kelly system may take longer to approach ruin, or exponentially decline to trivial bets, compared to alternative systems.
Wimpy 'I'd gladly pay you Tuesday for a hamburger today '
Hamburger moment problem
In World War I, Germany was considered the main culprit and provacateur
of the war. Therefore, it stirred the movement against Germans in
United States. Prior to the war, German-Americans were able to express
and promote their ethnic culture through the fine arts and language.
Once the war began, German-Americans came under public scrutiny and
ostracism. To raise support for the war, German culture was belittled
to establish the notion of superiority of America. Any traces of German
culture was erased in America. For example, instead of saying
“hamburger,” which has German roots, it was called “liberty sandwich.” 'Liberty Cabbage', and Anti-German Sentiment
Because of this perceived conflict of loyalties, the Wilson
administration was convinced that it had to mobilize public opinion in
support of the war. To influence public opinion, the federal government
embarked on its first ever domestic propaganda campaign.
The German word Hamburger, literally meaning "from the city of
Hamburg," begins to appear on American menus in the late 1800s during a
period of heavy German immigration.
Royal
White
Castle
Royal
White
Castle
What is liberty cabbage?
During World War I, due to concerns the American public would reject a product with a German name, American sauerkraut makers relabeled their product as "Liberty Cabbage" for the duration of the war.
Want some Freedom Fries with that Liberty Sandwich?
What is the Liberty sandwich again Popeye?
A sandwich made with a patty of ground meat usually in a roll or bun. [Short for Hamburger steak, after Hamburg.] Word History: The German word Hamburger, literally meaning "from the city of Hamburg," begins to appear on American menus in the late 1800s during a period of heavy German immigration.
During World War I, due to concerns the American public would reject a product with a German name, American sauerkraut makers relabeled their product as "Liberty Cabbage" for the duration of the war.
Want some Freedom Fries with that Liberty Sandwich?
What is the Liberty sandwich again Popeye?
A sandwich made with a patty of ground meat usually in a roll or bun. [Short for Hamburger steak, after Hamburg.] Word History: The German word Hamburger, literally meaning "from the city of Hamburg," begins to appear on American menus in the late 1800s during a period of heavy German immigration.
Almost everywhere
In measure theory (a branch of mathematical analysis), a property holds almost everywhere if, in a technical sense, the set for which the property holds takes up nearly all possibilities. The notion of "almost everywhere" is a companion notion to the concept of measure zero, and is analogous to the notion of "almost surely" in probability—a field which is largely based on measure theory.More specifically, a property holds almost everywhere if it holds for all elements in a set except a subset of measure zero,[1][2][3] or equivalently, if the set of elements for which the property holds is conull. In cases where the measure is not complete, it is sufficient that the set be contained within a set of measure zero. When discussing sets of real numbers, the Lebesgue measure is usually assumed unless otherwise stated.
The term almost everywhere is abbreviated a.e.;[4] in older literature p.p. is used, to stand for the equivalent French language phrase presque partout.[5]
A set with full measure is one whose complement is of measure zero. In probability theory, the terms almost surely, almost certain and almost always refer to events with probability 1 not necessarily including all of the outcomes[1]. These are exactly the sets of full measure in a probability space.
Occasionally, instead of saying that a property holds almost everywhere, it is said that the property holds for almost all elements (though the term almost all can also have other meanings).
The Steinitz exchange lemma is a basic theorem in linear algebra used, for example, to show that any two bases for a finite-dimensional vector space have the same number of elements. The result is named after the German mathematician Ernst Steinitz. The result is often called the Steinitz–Mac Lane exchange lemma, also recognizing the generalization[1]
by Saunders Mac Lane
of Steinitz's lemma to matroids.
E8 (mathematics)
In mathematics, E8 is any of several closely related exceptional simple Lie groups, linear algebraic groups or Lie algebras of dimension 248; the same notation is used for the corresponding root lattice, which has rank 8. The designation E8 comes from the Cartan–Killing classification of the complex simple Lie algebras, which fall into four infinite series labeled An, Bn, Cn, Dn, and five exceptional cases labeled E6, E7, E8, F4, and G2. The E8 algebra is the largest and most complicated of these exceptional cases.Rank (linear algebra)
In linear algebra, the rank of a matrix is the dimension of the vector space generated (or spanned) by its columns.[1] This corresponds to the maximal number of linearly independent columns... This, in turn, is identical to the dimension of the vector space spanned by its rows.[2] Rank is thus a measure of the "nondegenerateness" of the system of linear equations and linear transformation. There are multiple equivalent definitions of rank. A matrix's rank is one of its most fundamental characteristics.
is the dimension of the vector space generated (or spanned) by its columns.[1] This corresponds to the maximal number of linearly independent columns... This, in turn, is identical to the dimension of the vector space spanned by its rows.[2] Rank is thus a measure of the "nondegenerateness" of the system of linear equations and linear transformation. There are multiple equivalent definitions of rank. A matrix's rank is one of its most fundamental characteristics.In mathematics, Ricci calculus constitutes the rules of index notation and manipulation for tensors and tensor fields. It is also the modern name for what used to be called the absolute differential calculus (the foundation of tensor calculus), developed by Gregorio Ricci-Curbastro in 1887–1896, and subsequently popularized in a paper written with his pupil Tullio Levi-Civita in 1900.
In general relativity, Regge calculus is a formalism for producing simplicial approximations of spacetimes that are solutions to the Einstein field equation.
In mathematics and computer science, a matroid oracle is a subroutine through which an algorithm may access a matroid, an abstract combinatorial structure that can be used to describe the linear dependencies between vectors in a vector space or the spanning trees of a graph, among other applications.
The most commonly used oracle of this type is an independence oracle, a subroutine for testing whether a set of matroid elements is independent. Several other types of oracle have also been used; some of them have been shown to be weaker than independence oracles, some stronger, and some equivalent in computational power.[1]
Many algorithms that perform computations on matroids have been designed to take an oracle as input, allowing them to run efficiently without change on many different kinds of matroids, and without additional assumptions about what kind of matroid they are using. For instance, given an independence oracle for any matroid, it is possible to find the minimum weight basis of the matroid by applying a greedy algorithm that adds elements to the basis in sorted order by weight, using the independence oracle to test whether each element can be added.[2]
In computational complexity theory, the oracle model has led to unconditional lower bounds proving that certain matroid problems cannot be solved in polynomial time, without invoking unproved assumptions such as the assumption that P ≠ NP. Problems that have been shown to be hard in this way include testing whether a matroid is binary or uniform, or testing whether it contains certain fixed minors.
The most commonly used oracle of this type is an independence oracle, a subroutine for testing whether a set of matroid elements is independent. Several other types of oracle have also been used; some of them have been shown to be weaker than independence oracles, some stronger, and some equivalent in computational power.[1]
Many algorithms that perform computations on matroids have been designed to take an oracle as input, allowing them to run efficiently without change on many different kinds of matroids, and without additional assumptions about what kind of matroid they are using. For instance, given an independence oracle for any matroid, it is possible to find the minimum weight basis of the matroid by applying a greedy algorithm that adds elements to the basis in sorted order by weight, using the independence oracle to test whether each element can be added.[2]
In computational complexity theory, the oracle model has led to unconditional lower bounds proving that certain matroid problems cannot be solved in polynomial time, without invoking unproved assumptions such as the assumption that P ≠ NP. Problems that have been shown to be hard in this way include testing whether a matroid is binary or uniform, or testing whether it contains certain fixed minors.
Representation theory is a branch of mathematics that studies abstract algebraic structures by representing their elements as linear transformations of vector spaces, and studies modules
over these abstract algebraic structures. In essence, a representation
makes an abstract algebraic object more concrete by describing its
elements by matrices and its algebraic operations (for example, matrix
addition, matrix multiplication).
The theory of matrices and linear operators is well-understood, so
representations of more abstract objects in terms of familiar linear
algebra objects helps glean properties and sometimes simplify
calculations on more abstract theories.
In the study of the representation theory of Lie groups, the study of representations of SU(2) is fundamental to the study of representations of semisimple Lie groups.
Machine transitions are based on the current state and input symbol, and also the current topmost symbol of the stack. Symbols lower in the stack are not visible and have no immediate effect. Machine actions include pushing, popping, or replacing the stack top. A deterministic pushdown automaton has at most one legal transition for the same combination of input symbol, state, and top stack symbol. This is where it differs from the nondeterministic pushdown automaton.
Considered as a linear data structure, or more abstractly a sequential collection, the push and pop operations occur only at one end of the structure, referred to as the top of the stack. This data structure makes it possible to implement a stack as a singly linked list and a pointer to the top element. A stack may be implemented to have a bounded capacity. If the stack is full and does not contain enough space to accept an entity to be pushed, the stack is then considered to be in an overflow state. The pop operation removes an item from the top of the stack.
A stack is needed to implement depth-first search.
George Washington University
Washington, DC, USA
The main difference from other computers is that most of its instructions operate on a pushdown stack of numbers rather than numbers held in processor registers. With a foreground as thread mode and handler mode as background the thread privilege level with Selenium-webdriver that is Switched-on skyrmions for ARM Cortex stacked with Arduino innovations for hardware and software as:
Deterministic pushdown automaton
In automata theory, a deterministic pushdown automaton (DPDA or DPA) is a variation of the pushdown automaton. The class of deterministic pushdown automata accepts the deterministic context-free languages, a proper subset of context-free languages.[1]Machine transitions are based on the current state and input symbol, and also the current topmost symbol of the stack. Symbols lower in the stack are not visible and have no immediate effect. Machine actions include pushing, popping, or replacing the stack top. A deterministic pushdown automaton has at most one legal transition for the same combination of input symbol, state, and top stack symbol. This is where it differs from the nondeterministic pushdown automaton.
IT is a PUSH, POP... a Stack machine
Stack (abstract data type)
In computer science, a stack is an abstract data type that serves as a collection of elements, with two principal operations:- push, which adds an element to the collection, and
- pop, which removes the most recently added element that was not yet removed.
Considered as a linear data structure, or more abstractly a sequential collection, the push and pop operations occur only at one end of the structure, referred to as the top of the stack. This data structure makes it possible to implement a stack as a singly linked list and a pointer to the top element. A stack may be implemented to have a bounded capacity. If the stack is full and does not contain enough space to accept an entity to be pushed, the stack is then considered to be in an overflow state. The pop operation removes an item from the top of the stack.
A stack is needed to implement depth-first search.
George Washington University
Washington, DC, USA
JavaScript | string.slice()
A call graph (also known as a call multigraph) is a control flow graph, which represents calling relationships between subroutines in a computer program. Each node represents a procedure and each edge (f, g) indicates that procedure f calls procedure g. Thus, a cycle in the graph indicates recursive procedure calls. SSI Synchronous Serial Interface: JS Node, Vector = Node, Torsion Tensor, Twistor Theory Span of a set of Vectors in Knot Theory:Indexing, Slicing and Subsetting DataFrames in Python
In linear algebra, the linear span of a set S of vectors in a vector space is the smallest linear subspace that contains the set.
The critical path method (CPM), or critical path analysis (CPA), is an algorithm for scheduling a set of project activities. It is commonly used in conjunction with the program evaluation and review technique (PERT). A critical path is determined by identifying the longest stretch of dependent activities and measuring the time required to complete them from start to finish.
Span of control is the term used in business management, particularly human resource management.
Algorithm Efficiency
In computer science, computer engineering and programming language implementations, a stack machine is a type of computer. In some cases, the term refers to a software scheme that simulates a stack machine.
The main difference from other computers is that most of its instructions operate on a pushdown stack of numbers rather than numbers held in processor registers. Because the operands used in the instructions are always in a known location (the top of the stack), the instructions themselves do not require memory addresses or register numbers to supply their operands. This leads to an instruction set architecture (ISA) style known as a zero address format.[1]
Stacks are not unique to stack machines; most programming languages make extensive use of stacks to support subroutines and method calls. For this reason, stack machines more closely mimic the inner workings of the programs that run on them, assuming the programs are written in high level languages. This has led to a number of central processor unit designs that implement stack machines in order to provide higher performance. In practice, however, these designs have been outperformed by the traditional register machine systems, and have remained a niche player in the market.
Pushdown on a control register stack pointer to address algorithmic efficiency as a property of an algorithm which relates to the number of computational resources used by the algorithm. Considerations of a Control register, stack pointer and call graph:
srcSlice: very efficient and scalable forward static slicing
A stack register is a computer central processor register whose purpose is to keep track of a call stack. A semaphore is a variable or abstract data type used to control access to a common resource by multiple processes in a concurrent system such as a multitasking operating system.
PROCEDURE ARGUMENTS
The main difference from other computers is that most of its instructions operate on a pushdown stack of numbers rather than numbers held in processor registers. Because the operands used in the instructions are always in a known location (the top of the stack), the instructions themselves do not require memory addresses or register numbers to supply their operands. This leads to an instruction set architecture (ISA) style known as a zero address format.[1]
Stacks are not unique to stack machines; most programming languages make extensive use of stacks to support subroutines and method calls. For this reason, stack machines more closely mimic the inner workings of the programs that run on them, assuming the programs are written in high level languages. This has led to a number of central processor unit designs that implement stack machines in order to provide higher performance. In practice, however, these designs have been outperformed by the traditional register machine systems, and have remained a niche player in the market.
Pushdown on a control register stack pointer to address algorithmic efficiency as a property of an algorithm which relates to the number of computational resources used by the algorithm. Considerations of a Control register, stack pointer and call graph:
srcSlice: very efficient and scalable forward static slicing
A stack register is a computer central processor register whose purpose is to keep track of a call stack. A semaphore is a variable or abstract data type used to control access to a common resource by multiple processes in a concurrent system such as a multitasking operating system.
Procedure Parameters and Arguments (Visual Basic)
In computing, a procedural parameter is a parameter of a procedure that is itself a procedure.PROCEDURE ARGUMENTS
De novo synthesis refers to the synthesis of complex molecules from simple molecules such as sugars or amino acids, as opposed to recycling after partial degradation. For example, nucleotides are not needed in the diet as they can be constructed from small precursor molecules such as formate and aspartate. Methionine, on the other hand, is needed in the diet because while it can be degraded to and then regenerated from homocysteine, it cannot be synthesized de novo.
De novo is a Latin phrase, literally translating to "from the new", but implying "anew", "from scratch", or "from the beginning."
De novo is a Latin phrase, literally translating to "from the new", but implying "anew", "from scratch", or "from the beginning."
Corticospinal mirror neurons
George Santayana.
Those who cannot remember the past are condemned to repeat it
The Monday Campaigns is a non-profit public health initiative associated with Johns Hopkins, Columbia and Syracuse universities that dedicates the first day of every week to health. Every Monday, individuals and organizations join together to commit to the healthy behaviors that can help end chronic preventable diseases.
The Monday Campaigns is a non-profit public health initiative associated with Johns Hopkins, Columbia and Syracuse universities that dedicates the first day of every week to health. Every Monday, individuals and organizations join together to commit to the healthy behaviors that can help end chronic preventable diseases.
Memories Can Be Injected and Survive Amputation and Metamorphosis
Posted By Marco Altamirano on Dec 13, 2019
Alcohol use and TBI are closely related. Up to two-thirds of people with TBI have a history of alcohol abuse or risky drinking. ... Drinking
increases your chances of getting injured again, makes cognitive
(thinking) problems worse, and increases your chances of having
emotional problems such as depression.
People
talk funny TBI or not sometimes like a French Cajun Creole translator
for Scotch Gaelic, especially when bag pipes and zydeco music are
involved, like for some sort of Boxing day song.
Alcohol Use After Traumatic Brain Injury
A Drunkards walk also known as a...
Random walk
A random walk is a mathematical object, known as a stochastic or random process, that describes a path that consists of a succession of random steps on some mathematical space such as the integers... Will the person ever get back to the original starting point of the walk? This is the 2-dimensional equivalent of the level-crossing problem discussed above. In 1921 George Pólya proved that the person almost surely would in a 2-dimensional random walk, but for 3 dimensions or higher, the probability of returning to the origin decreases as the number of dimensions increases. In 3 dimensions, the probability decreases to roughly 34%.[10] The mathematician Shizuo Kakutani was known to refer to this result with the following quote: "A drunk man will find his way home, but a drunk bird may get lost forever".[11]
In statistics, the bias (or bias function) of an estimator is the difference between this estimator's expected value and the true value of the parameter being estimated. An estimator or decision rule with zero bias is called unbiased. In statistics, "bias" is an objective property of an estimator. Unlike the ordinary English use of the term "bias", it is not pejorative even though it's not a desired property.
psychoanalyst Jacques Lacan found inspiration from the Borromean rings as a model for his topology of human subjectivity, with each ring representing a fundamental Lacanian component of reality (the "real", the "imaginary", and the "symbolic")
Hadamard three-circle theorem
Motor capacitor
Single-phase Induction Motors
Faraday's Law
Eddy current
Faraday's law of induction
Faraday paradox
Turing's method
Riemann–Siegel formula
Turing test
Riemann–Siegel theta function
Infinite monkey theorem
The
company expressed regret at the embarrassing communications it sent to
investigators on Thursday, which included a comment that “this airplane
is designed by clowns, who are in turn supervised by monkeys.”
Realativity, Induction...
Relativistic electromagnetism
In literature, the competent man is a stock character who exhibits a very wide range of abilities and knowledge, making him a form of polymath. While not the first to use such a character type, the heroes and heroines of Robert A. Heinlein's fiction (with Jubal Harshaw being a prime example) generally have a wide range of abilities, and one of Heinlein's characters, Lazarus Long, gives a wide summary of requirements:
A human being should be able to change a diaper, plan an invasion, butcher a hog, conn a ship, design a building, write a sonnet, balance accounts, build a wall, set a bone, comfort the dying, take orders, give orders, cooperate, act alone, solve equations, analyse a new problem, pitch manure, program a computer, cook a tasty meal, fight efficiently, die gallantly. Specialization is for insects.
The competent man, more often than not, is written without explaining how he achieved his wide range of skills and abilities. When such characters are young, there is often not much explanation as to how they acquired so many skills at an early age.— Robert Heinlein, Time Enough for Love
History
Examples of early modern competent heroes include the protagonists of George Bernard Shaw, like Henry Higgins in Pygmalion and Caesar in Caesar and Cleopatra, as well as the citizen soldiers in Rudyard Kipling's "The Army of a Dream".Many non-superpowered comic book characters are written as hyper-competent characters due to the perception that they would simply be considered underpowered otherwise. Batman, for example, is typically depicted as a member of the Justice League of America alongside Superman, Wonder Woman, and Green Lantern, all of whom are superpowered while he lacks superhuman powers of any kind. As a result, despite his original depiction as a vigilante, modern depictions of Batman portray him as having achieved the peak-human possibility in things physical and intellectual. The same treatment has been applied to Lex Luthor, who has always been Superman's archenemy despite the former's total lack of superhuman powers.
See also
- Mary Sue
- Jack of all trades, master of none
- breaking the status quo
Ed Smith And The Imagination Machine: The Untold Story Of A Black Video Game Pioneer
At APF in the 1970s, as the second-known African-American video game engineer, he helped create an industry.
A software bug is an
error, flaw, failure or fault in a computer program or system that
causes it to produce an incorrect or unexpected result, or to behave in
unintended ways.
Insects in the family Elateridae are commonly called click beetles (or "typical click beetles" to distinguish them from the related families Cerophytidae and Eucnemidae). Other names include elaters, snapping beetles, spring beetles or skipjacks. This family was defined by William Elford Leach (1790–1836) in 1815.
The soldier beetles (Cantharidae) are relatively soft-bodied, straight-sided beetles. They are cosmopolitan in distribution. One of the first described species has a color pattern reminiscent of the red coats of early British soldiers, hence the common name. They are also known commonly as leatherwings because of their soft elytra.
Historically, these beetles were placed in a superfamily "Cantharoidea", which has been subsumed by the superfamily Elateroidea; the name is still sometimes used as a rankless grouping, including the families Cantharidae, Drilidae, Lampyridae, Lycidae, Omalisidae, Omethidae (which includes Telegeusidae), Phengodidae, and Rhagophthalmidae.
Reproduction
Large males of the soldier beetle exercise choice for larger females. Body size correlates with the abilities of males to secure females, and of females to evade male
Luciferin (from the Latin lucifer, "light-bringer") is a generic term for the light-emitting compound found in organisms that generate bioluminescence.
Bioluminescent bacteria
GloFish
Illustrated Glossary of Organic Chemistry
Tiny Conspiracies: Cell-to-Cell Communication in Bacteria by Bonnie Bassler
The purpose of this paper is to introduce the idea of triangular Ram-sey numbers and provide values as well as upper and lower bounds forthem. To do this, the combinatorial game Mines is introduced; after somenecessary theorems about triangular sets are proved.
Contributor
The
body’s microbial community may influence the brain and behavior,
perhaps even playing a role in dementia, autism and other disorders.
How bacteria "talk" - Bonnie Bassler
Messing with Bacterial Quorum Sensing
Juan E. González* and Neela D. Keshavan
Gut feelings: How food affects your mood
Uma Naidoo, MDContributor
Psychobiotics and the Manipulation of Bacteria–Gut–Brain Signals
Amar Sarkar,1 Soili M. Lehto,2,3 Siobhán Harty,1 Timothy G. Dinan,4 John F. Cryan,5 and Philip W.J. Burnet6,⁎
Organoids: A new window into disease, development and discovery
November 7, 2017
Scientists have found ways of culturing organ-specific tissue from stem cells that could change the way diseases are studied and treated.
Human-like brain waves detected in mini brains grown in a dish
The organoids formed networks and produced electrical activity resembling that of six to 10 month old infants.
Glia, also called glial
cells or neuroglia, are non-neuronal cells in the central nervous
system (brain and spinal cord) and the peripheral nervous system.
as far as
Popeye is a Python module for estimating population receptive fields
from fMRI data.
The Grüneisen parameter,
γ, named after Eduard Grüneisen, describes the effect that changing the
volume of a crystal lattice has on its vibrational properties, and, as a
consequence, the effect that changing temperature has on the size or
dynamics of the lattice.
Tissue engineering
Golgi staining was used by Spanish neuroanatomist Santiago Ramón y
Cajal (1852–1934) to discover a number of novel facts about the
organization of the nervous system, inspiring the birth of the neuron doctrine.
Ultimately, Ramon y Cajal improved the technique by using a method he
termed "double impregnation." Ramon y Cajal's staining technique, still
in use, is called Cajal's Stain. Golgi's method
is a silver staining technique that is used to visualize nervous tissue
under light microscopy. The method was discovered by Camillo Golgi, an
Italian physician and scientist, who published the first picture made
with the technique in 1873.
Tissue engineering
The Persistence and Transience of Memory
- Blake A. Richards
- Paul W. Frankland
In computer science and operations research, a genetic algorithm (GA)
is a metaheuristic inspired by the process of natural selection that
belongs to the larger class of evolutionary algorithms (EA).
PHAT Python API reference
Due to the Hamming distance properties of Gray codes, they are sometimes used in genetic algorithms. They are very useful in this field, since mutations in the code allow for mostly incremental changes, but occasionally a single bit-change can cause a big leap and lead to new properties.
In information theory, the Hamming distance
between two strings of equal length is the number of positions at which
the corresponding symbols are different. In other words, it measures
the minimum number of substitutions required to change one string into the other, or the minimum number of errors
that could have transformed one string into the other. In a more
general context, the Hamming distance is one of several string metrics
for measuring the edit distance between two sequences. It is named after
the American mathematician Richard Hamming (1915-1998).
Keras: The Python Deep Learning library
Keras is an open source neural network library written in Python
Parentification is the process of role reversal whereby a child is obliged to act as parent to their own parent or sibling.
In extreme cases, the child is used to fill the void of the alienating parent's (sibling's) emotional life.
Katya Walter has shown that the
Fu Xi Earlier Heaven Ho Tu arrangement
of the 64 hexagrams can represent the DNA genetic code:
Since the DNA genetic code can be represented by 4 things taken 3 at a time, or (2x2) x (2x2) x (2x2) = 64
Hamming code
Hamming(7,4)
FreeBSD
is a free and open-source Unix-like operating system descended from the
Berkeley Software Distribution (BSD), which was based on Research Unix.
Selenium is a portable framework for testing web applications.
Selenium provides a playback tool for authoring functional tests without
the need to learn a test scripting language.
TensorFlow
is a free and open-source software library for dataflow and
differentiable programming across a range of tasks. It is a symbolic
math library, and is also used for machine learning applications such as neural networks. It is used for both research and production at Google.
In mathematics, a tensor is an algebraic
object related to a vector space and its dual space that can be defined
in several different ways, often a scalar, tangent vector at a point, a
cotangent vector (dual vector) at a point or a multi-linear map from
vector spaces to a resulting vector space.
hypermethylation
- (chemistry) The addition of a methyl group to a molecule.
- (genetics) The addition of a methyl group to cytosine and adenine residues in DNA that leads to the epigenetic modification of DNA and the reduction of gene expression and protein production.
- Transcription is the process in which a gene's DNA sequence is copied (transcribed) to make an RNA molecule.
- RNA polymerase is the main transcription enzyme.
- Transcription begins when RNA polymerase binds to a promoter sequence near the beginning of a gene (directly or through helper proteins).
- RNA polymerase uses one of the DNA strands (the template strand) as a template to make a new, complementary RNA molecule.
- Transcription ends in a process called termination. Termination depends on sequences in the RNA, which signal that the transcript is finished.
Seneca is a microservices toolkit for Node.js
Psi or the initials PSI or Ψ may refer to:
Mathematics
- Dedekind psi function
- Probability of ultimate ruin, in ruin theory
- Supergolden ratio
Stream function, in two-dimensional flows
Computing
Program-specific information, part of the MPEG transport stream protocol
Psi (instant messaging client), XMPP client program
PSGI/Plack
Superglue interface between perl web application frameworks and web servers, just like Perl is the duct tape of the internet.
PSGI or Perl Web Server Gateway Interface
is an interface between web servers and web applications and frameworks
written in the Perl programming language that allows writing portable
applications that can be run as standalone servers or using CGI, FastCGI, mod_perl, et al. It is inspired by the Web Server Gateway Interface for Python, Rack for Ruby and JSGI for JavaScript.
A PSGI application is a Perl subroutine that accepts arguments as a
single hash reference and returns a reference to an array of three
elements: an HTTP status code, a reference to an array of HTTP headers
and a reference to an array of HTTP body lines (usually a generated HTML
document) or a filehandle-like object.
In mathematics, the Wronskian (or Wrońskian) is a determinant introduced by Józef Hoene-Wroński (1812) and named by Thomas Muir (1882, Chapter XVIII). It is used in the study of differential equations, where it can sometimes show linear independence in a set of solutions.
∀ universal quantifier (there exists) ∃ existential quantifier (for all or for some)
Turing Machine, Oracle Machine
Lambda, Sheer Matrix, Sheer Mapping, Shear Stress, Flat (geometry)...
Robert Moses is empowering students in an epoch journey, sort of like that dude from the book of Numbers in the Bible:
Peano existence theorem
In mathematics, specifically in the study of ordinary differential equations, the Peano existence theorem, Peano theorem or Cauchy–Peano theorem, named after Giuseppe Peano and Augustin-Louis Cauchy, is a fundamental theorem which guarantees the existence of solutions to certain initial value problems.Shear mapping
Shear matrix
Flat (geometry)
A flat is the British English equivalent of the word apartment. A flat
is a single-family suite of rooms including a kitchen and at least one
bathroom situated in a building with multiple such suites, a flat is generally a rental property.
How Poor Americans Get Exploited by Their Landlords
Mar 21, 2019
The Home Owners' Loan Corporation (HOLC) was a government-sponsored corporation created as part of the New Deal. The corporation was established in 1933 by the Home Owners' Loan Corporation Act under the leadership of President Franklin D. Roosevelt.[2] Its purpose was to refinance home mortgages currently in default to prevent foreclosure.
Incredible!
The Home Owner's Loan Corporation
Red was the color used to indicated these "Fourth Grade" areas on the map and, thus, a new term came into our vocabulary: "redlining."America’s housing crisis, summed up in 3 charts
Rents are rising while incomes stagnate. It’s an “unprecedented” situation, as a new Harvard report details.
Textiles were 13.7% more expensive in Boston than in Manchester in
1870 as rice in the East danced along the convergence in agricultural
prices. Shipping efficiency produced convergence of the prices of three
basic input factors, wages, rents and interest rates. Swedish economist
theorized decreased shipping cost creates global convergence of
commodity prices from output of labor, land and capitol to derive wages,
rates and interest. By 1913 (1870-1913) U.S. rent rose by 248.9% while
British rent fell 43.3%.
There was an old woman who lived in a shoe.
She had so many children, she didn't know what to do. She gave them some
broth without any bread; Then whipped them all soundly and put them to
bed.
More Americans are quitting their jobs than ever.
Between 1870 and 1913 American rent rose by 248.9% while British rent fell 43.3%
Tariffs and wages An inconvenient iota of truth
The third in our series looks at the Stolper-Samuelson theorem
Real Estate
The End of the Global Housing Boom
After a years-long surge in global capitals, property prices are starting to head lower. From Sydney to Toronto, here’s a look at what’s ahead.
The Heckscher-Ohlin Trade Model
What is the Smoot Hawley tariff and what was its effect?
Smoot-Hawley Tariff Act, formally United States Tariff Act of 1930, also called Hawley-Smoot Tariff Act, U.S. legislation (June 17, 1930) that raised import duties to protect American businesses and farmers, adding considerable strain to the international economic climate of the Great Depression.
There are many statistical measures that show how productive the U.S. is.
Here's How America Uses Its Land
By Dave Merrill and Lauren Leatherby
July 31, 2018
The Calumet and Hecla Mining Company was a major copper-mining company based within Michigan's Copper Country. In the 19th century, the company paid out more than $72 million in shareholder dividends, more than any other mining company in the United States during that period.
Princess Alexandra and Princess Dagmar, who pulled off the dynastic coup of the 19th century by marrying the heirs to both the British and Russian thrones. Following the invasion of their native Denmark by Prussia in 1864 during the Wars of German Unification, the sisters became the core of an anti-Prussian coalition that prefigured the great anti-German alliance of 1914. Their sons, King George V and Tsar Nicholas II were also close friends. The programme also looks at the tangled relationship between the German Kaiser and his English mother, Vicky – the oldest daughter of Queen Victoria. Disabled from birth, Kaiser Wilhelm had a complex love/hate attitude towards Vicky, which transferred itself to Britain as a whole, strongly influencing his foreign policy
Now past the PBS of the cousins at war, consider here in the US during the same time:
Jacob Henry Schiff was a Jewish-American banker, businessman, and philanthropist. Among many other things, he helped finance the expansion of American railroads and the Japanese military efforts against Tsarist Russia in the Russo-Japanese War. In 1919, G.H. (Bert) Walker, a St. Louis-born, British-schooled operative of British and Morgan bankers, set up a private bank for E.H. Harriman’s sons, Averell and Roland, W.A. Harriman and Company. E.H. Harriman acquiring the bankrupt Union Pacific Railroad, financed through the British royal family’s private financier, Sir Ernst Cassel, Cassel’s New York partner Jacob Schiff, and members of the Rockefeller family. Like everything else on Wall Street, the financiers traded on what others had created. A banker and philanthropist, Jacob H. Schiff secured European funding to build America’s railroads, mines, and other enterprises. He helped transform the United States into the world’s leading industrialized economy.
A Russian Warship Was Discovered with an Estimated $130 Billion in Gold on Board
How did the Russo Japanese War impact Japan's modernization?
The Russo-Japanese War was a brief conflict but created significant problems for the tsarist regime. It was triggered by Nicholas II and his wish to expand the Russian empire in Asia. ... Even more telling was the economic impact the war had on the Russian economy, which fanned the flames of revolution in 1905.
Tsar Nicholas II's murder 100 years on: The terrible fate of Russia’s imperial family
In 1926, Bert brought his son-in-law, Prescott Bush, into this enterprise, Prescott and Roland Harriman having sworn lifetime blood oaths to each other as members of Yale’s secret satanic Skull and Bones society. Beginning in 1920, W.A. Harriman and Company under Bert Walker’s direction, began looting post-World War I Germany, acquiring control over shipping (the Hamburg-America ship line), and buying into steel production and raw materials. When the Depression hit, W.A. Harriman merged with Brown Brothers, the British family investment firm of Montagu Norman, the pro-Nazi head of the Bank of England. Brown Brothers Harriman was the largest private investment bank in the United States, and Prescott Bush was installed as its managing director. According to his account, Prescott presided over the weekly Thursday partners meeting at the firm, assisted by “silent and properly attired British floor attendants.”
Prescott Bush presided over a banking complex tightly interwoven with the funding centers for Adolf Hitler and the Nazi party. Most notable was their subsidiary, the Union Banking Corporation (UBC), a money-management front for Fritz Thyssen, the leading German steel and coal tycoon. Brown Brothers Harriman was also the bank of the Consolidated Silesian Steel Company, which included Thyssen’s Nazi business partner Friedrich Flick among its owners, and utilized slave labor from Auschwitz in its operations. In addition, Bush was the director of a number of companies associated with Thyssen, including the Silesian American Corporation. Thyssen, by his own account, was the chief financier of Hitler’s rise to power in Germany. By the late 1930s, Brown Brothers Harriman had bought and shipped millions of dollars of gold, fuel, steel, coal, and U.S. Treasury bonds to Germany, both feeding and financing Hitler’s war build-up.
Tariffs and wages An inconvenient iota of truth
The third in our series looks at the Stolper-Samuelson theorem
Real Estate
The End of the Global Housing Boom
After a years-long surge in global capitals, property prices are starting to head lower. From Sydney to Toronto, here’s a look at what’s ahead.
The Heckscher-Ohlin Trade Model
What is the Smoot Hawley tariff and what was its effect?
Smoot-Hawley Tariff Act, formally United States Tariff Act of 1930, also called Hawley-Smoot Tariff Act, U.S. legislation (June 17, 1930) that raised import duties to protect American businesses and farmers, adding considerable strain to the international economic climate of the Great Depression.
There are many statistical measures that show how productive the U.S. is.
Here's How America Uses Its Land
By Dave Merrill and Lauren Leatherby
July 31, 2018
The Calumet and Hecla Mining Company was a major copper-mining company based within Michigan's Copper Country. In the 19th century, the company paid out more than $72 million in shareholder dividends, more than any other mining company in the United States during that period.
Princess Alexandra and Princess Dagmar, who pulled off the dynastic coup of the 19th century by marrying the heirs to both the British and Russian thrones. Following the invasion of their native Denmark by Prussia in 1864 during the Wars of German Unification, the sisters became the core of an anti-Prussian coalition that prefigured the great anti-German alliance of 1914. Their sons, King George V and Tsar Nicholas II were also close friends. The programme also looks at the tangled relationship between the German Kaiser and his English mother, Vicky – the oldest daughter of Queen Victoria. Disabled from birth, Kaiser Wilhelm had a complex love/hate attitude towards Vicky, which transferred itself to Britain as a whole, strongly influencing his foreign policy
Now past the PBS of the cousins at war, consider here in the US during the same time:
Jacob Henry Schiff was a Jewish-American banker, businessman, and philanthropist. Among many other things, he helped finance the expansion of American railroads and the Japanese military efforts against Tsarist Russia in the Russo-Japanese War. In 1919, G.H. (Bert) Walker, a St. Louis-born, British-schooled operative of British and Morgan bankers, set up a private bank for E.H. Harriman’s sons, Averell and Roland, W.A. Harriman and Company. E.H. Harriman acquiring the bankrupt Union Pacific Railroad, financed through the British royal family’s private financier, Sir Ernst Cassel, Cassel’s New York partner Jacob Schiff, and members of the Rockefeller family. Like everything else on Wall Street, the financiers traded on what others had created. A banker and philanthropist, Jacob H. Schiff secured European funding to build America’s railroads, mines, and other enterprises. He helped transform the United States into the world’s leading industrialized economy.
A Russian Warship Was Discovered with an Estimated $130 Billion in Gold on Board
How did the Russo Japanese War impact Japan's modernization?
The Russo-Japanese War was a brief conflict but created significant problems for the tsarist regime. It was triggered by Nicholas II and his wish to expand the Russian empire in Asia. ... Even more telling was the economic impact the war had on the Russian economy, which fanned the flames of revolution in 1905.
Tsar Nicholas II's murder 100 years on: The terrible fate of Russia’s imperial family
In 1926, Bert brought his son-in-law, Prescott Bush, into this enterprise, Prescott and Roland Harriman having sworn lifetime blood oaths to each other as members of Yale’s secret satanic Skull and Bones society. Beginning in 1920, W.A. Harriman and Company under Bert Walker’s direction, began looting post-World War I Germany, acquiring control over shipping (the Hamburg-America ship line), and buying into steel production and raw materials. When the Depression hit, W.A. Harriman merged with Brown Brothers, the British family investment firm of Montagu Norman, the pro-Nazi head of the Bank of England. Brown Brothers Harriman was the largest private investment bank in the United States, and Prescott Bush was installed as its managing director. According to his account, Prescott presided over the weekly Thursday partners meeting at the firm, assisted by “silent and properly attired British floor attendants.”
Prescott Bush presided over a banking complex tightly interwoven with the funding centers for Adolf Hitler and the Nazi party. Most notable was their subsidiary, the Union Banking Corporation (UBC), a money-management front for Fritz Thyssen, the leading German steel and coal tycoon. Brown Brothers Harriman was also the bank of the Consolidated Silesian Steel Company, which included Thyssen’s Nazi business partner Friedrich Flick among its owners, and utilized slave labor from Auschwitz in its operations. In addition, Bush was the director of a number of companies associated with Thyssen, including the Silesian American Corporation. Thyssen, by his own account, was the chief financier of Hitler’s rise to power in Germany. By the late 1930s, Brown Brothers Harriman had bought and shipped millions of dollars of gold, fuel, steel, coal, and U.S. Treasury bonds to Germany, both feeding and financing Hitler’s war build-up.
The Stolper-Samuelson theorem (SST)
simply suggests that, in any particular country, a rise in the relative
(producer) prices of the labour intensive good will make labour better
off and capital worse-off, and vice-versa, provided that some amount of
each good is being produced.
Textiles were 13.7% more expensive in Boston than in Manchester in 1870 as rice in the East danced along the convergence in agricultural prices. Shipping efficiency produced convergence of the prices of three basic input factors, wages, rents and interest rates. Swedish economist theorized decreased shipping cost creates global convergence of commodity prices from output of labor, land and capitol to derive wages, rates and interest. By 1913 (1870-1913) U.S. rent rose by 248.9% while British rent fell 43.3%. Mind how commodities dance in global trade as Serenity Sells solicits Commodity Pool Operations to couple WIOA and the Texas Able program with a 501 c (4) Welfare charter with mission to address the least among you to serve the great state of Texas.
The Stolper-Samuelson Theorem
The Stolper-Samuelson theorem demonstrates how changes in output prices affect the prices of the factors when positive production and zero economic profit are maintained in each industry . It is useful in analyzing the effects on factor income, either when countries move from autarky to free trade or when tariffs or other government regulations are imposed within the context of a H-O model.
Business Day
W. F. Stolper, Trade Theory Economist, Is Dead at 89
By LOUIS UCHITELLEAPRIL 4, 2002
Textiles were 13.7% more expensive in Boston than in Manchester in 1870 as rice in the East danced along the convergence in agricultural prices. Shipping efficiency produced convergence of the prices of three basic input factors, wages, rents and interest rates. Swedish economist theorized decreased shipping cost creates global convergence of commodity prices from output of labor, land and capitol to derive wages, rates and interest. By 1913 (1870-1913) U.S. rent rose by 248.9% while British rent fell 43.3%. Mind how commodities dance in global trade as Serenity Sells solicits Commodity Pool Operations to couple WIOA and the Texas Able program with a 501 c (4) Welfare charter with mission to address the least among you to serve the great state of Texas.
The Stolper-Samuelson Theorem
The Stolper-Samuelson theorem demonstrates how changes in output prices affect the prices of the factors when positive production and zero economic profit are maintained in each industry . It is useful in analyzing the effects on factor income, either when countries move from autarky to free trade or when tariffs or other government regulations are imposed within the context of a H-O model.
Business Day
W. F. Stolper, Trade Theory Economist, Is Dead at 89
By LOUIS UCHITELLEAPRIL 4, 2002
The War Between the Gettys
A RAGING and bizarre family fight is buffeting the Sarah C. Getty Trust, the chief beneficiary of last year’s sale of Getty Oil to Texaco. At stake is control of about $4 billion in assets that, even after huge capital gains taxes, will still stack up at around $3 billion.
The Heckscher–Ohlin model (H–O model) is a general equilibrium mathematical model of international trade, developed by Eli Heckscher and Bertil Ohlin at the Stockholm School of Economics. It builds on David Ricardo's theory of comparative advantage by predicting patterns of commerce and production based on the factor endowments of a trading region. The model essentially says that countries export products that use their abundant and cheap factors of production, and import products that use the countries' scarce factors
"Plank" is the term often given to the components of the political platform – the opinions and viewpoints about individual topics, as held by a party, person, or organization.
A political party platform or program is a formal set of principal goals which are supported by a political party or individual candidate,
in order to appeal to the general public, for the ultimate purpose of
garnering the general public's support and votes about complicated
topics or issues. "Plank" is the term often given to the components of
the political platform – the opinions and viewpoints about individual
topics, as held by a party, person, or organization.
Matthew 7:5 is the fifth verse of the seventh chapter of the Gospel of Matthew in the New Testament and is part of the Sermon on the Mount. This verse continues the discussion of judgmentalism.
You hypocrite! First remove the beam out of your own eye, and then you can see clearly to remove the speck out of your brother's eye. This verse continues the metaphor of a person with a plank in their own eye who criticizes someone for a speck in that person's eye.
walk the plank
To be forced to accept the consequences of something. The phrase refers to the idea of pirates forcing their prisoners to walk off a plank on a ship and ultimately drown in the ocean. The person who's embezzling money from the company will have to walk the plank once their identity is discovered.
A bully pulpit is a conspicuous position that provides an
opportunity to speak out and be listened to.
This term was coined by United States President Theodore Roosevelt, who
referred to his office as a "bully pulpit", by which he meant a terrific
platform from which to advocate an agenda.
The idea of corporate election expresses a Christian soteriological view that understands Christian salvation as based on "God choosing in Christ a people whom he destines to be holy and blameless in his sight". Put another way, "Election is the corporate choice of the church 'in Christ.'" Paul Marston and Roger Forster state that the "central idea in the election of the church may be seen from Ephesians 1:4": "For he [God] chose us [the Church] in him [Christ], before the creation of the world to be holy and blameless in his sight." William Klein adds:
The counter-view to unconditional election is conditional election, the belief that God chooses for eternal salvation those whom he foreknows will exercise their free will to respond to God's prevenient grace with faith in Christ.
The idea of corporate election expresses a Christian soteriological view that understands Christian salvation as based on "God choosing in Christ a people whom he destines to be holy and blameless in his sight". Put another way, "Election is the corporate choice of the church 'in Christ.'" Paul Marston and Roger Forster state that the "central idea in the election of the church may be seen from Ephesians 1:4": "For he [God] chose us [the Church] in him [Christ], before the creation of the world to be holy and blameless in his sight." William Klein adds:
Here [in Ephesians 1:3-4] Paul states that God chose Christians in Christ before the creation of the world to be holy and blameless in his sight. The "chosen ones" designate the corporate group to whom Paul writes with himself (and presumably all Christians) included: God chose us. The focus is not on the selection of individuals, but the group of those chosen. As Westcott notes, "He chose us (i.e. Christians as a body, v. 4) for Himself out of the world." Paul specifies the timing of this choice—it was pretemporal, before the world was created. God made the choice "in him" (that is, "in Christ"). In other words, Christ is the principal elected one, and God has chosen a corporate body to be included in him."Unconditional election (also known as unconditional grace) is a Lutheran and Reformed doctrine relating to Predestination that describes the actions and motives of God in eternity past, before He created the world, where he predestinated some people to receive salvation, the elect, and the rest he left to continue in their sins and receive the just punishment, eternal damnation, for their transgressions of God's law as outlined in the old and new Testaments of the Bible. God made these choices according to his own purposes apart from any conditions or qualities related to those persons.
The counter-view to unconditional election is conditional election, the belief that God chooses for eternal salvation those whom he foreknows will exercise their free will to respond to God's prevenient grace with faith in Christ.
China Warns Against Travel to Australia, Citing Discrimination
By Reuters
Hallie Gu, Keith Zhai, Jing Xu
Ethics of Angora Rabbit farms in China v. Prison Goat milk farms in Colorado, Pioneering codebreaker Elizebeth Friedman, and bio engineered goats for recombinant spider silk in BioSteel manufacturing for bullet proof vests
If hours and hours of childhood memories watching Bugs Bunny has taught me anything...
Little Bunny foo, foo aka Angora Rabbit
To make someone annoyed or angry: “Gavin may seem unflappable, but I know a way to get his goat.” This expression comes from a tradition in horse racing. Thought to have a calming effect on high-strung thoroughbreds, a goat was placed in the horse's stall on the night before the race. Unscrupulous opponents would then steal the goat in an effort to upset the horse and cause it to lose the race.
These goats are from China, or Asia.
A prison farm with Angora goats, Cashmere goats, Silkie chickens and Angora rabbits may help shepherd lessons of ethics to assist in rehabilitating.
https://usserviceanimals.org/
If the angora rabbit, silkie chicken angora goat and cashmere goats are registered as emotional service animals, a prisoner whom treats the animal better than say the Chinese whom have committed ethical violations, then a level of rehabilitation may be proposed as facilitated as such.
My uncle David Schubert participated in a Catholic Prison Ministries program
Goats may be kept for milk, meat, or fiber (or a combination thereof).
Both Angora and Cashmere goats are raised for fiber, but differ in both
fiber qualities and methods of fiber harvest. Angora goats produce
mohair. Fiber from non-Angora goats is Cashmere. Note that rabbits, not
Angora goats, produce Angora fiber.
Little Bunny foo, foo aka Angora Rabbit
5 Shocking Reasons You Should Skip Angora Wool This Winter
What would Bugs Bunny do?get someone's goat
To make someone annoyed or angry: “Gavin may seem unflappable, but I know a way to get his goat.” This expression comes from a tradition in horse racing. Thought to have a calming effect on high-strung thoroughbreds, a goat was placed in the horse's stall on the night before the race. Unscrupulous opponents would then steal the goat in an effort to upset the horse and cause it to lose the race.
These goats are from China, or Asia.
A prison farm with Angora goats, Cashmere goats, Silkie chickens and Angora rabbits may help shepherd lessons of ethics to assist in rehabilitating.
https://usserviceanimals.org/
If the angora rabbit, silkie chicken angora goat and cashmere goats are registered as emotional service animals, a prisoner whom treats the animal better than say the Chinese whom have committed ethical violations, then a level of rehabilitation may be proposed as facilitated as such.
My uncle David Schubert participated in a Catholic Prison Ministries program
Food For Thought
Angora Goat Shearing
Cheese Made Using Prison Labor Cut from Whole Foods
A business plan may be proposed to Central Market in Austin Texas as part of a farm to market justified budget.
Central
Market in Austin Texas may be contacted and a business plan that models
with Haystack farms may be developed, however if we get the Catholic's
and Prison ministries involved and propose service animals to raise the
bar on ethics for treatment of rabbits, goats, chickens and humans, we
may facilitate a healthy market branding exercise. Hey, what kind of
farm is this anywho?
This Woman Saved the Americas From the Nazis
Pioneering codebreaker Elizebeth Friedman, a poet and mother of two, smashed spy rings by solving secret messages.
Elizebeth cut her teeth as a codebreaker during Prohibition in the unlikely role of interdicting rumrunners. Set the scene for us—and describe how she reacted to becoming a minor celebrity.
Federal Prison Industries, Inc. (FPI), doing business as UNICOR (stylized as unicor) since 1977, is a wholly owned United States government corporation created in 1934 as a prison labor program for inmates within the Federal Bureau of Prisons, and a component of the Department of Justice. It is headquartered in Washington, DC.
Federal Prison Industries (FPI) is the largest inmate-training program
operated by the Bureau of Prisons
and one of the most important correctional
programs in the Department of Justice. Created by Federal statute
in 1934, FPI operates as a wholly owned,
self-sustaining government corporation under the trade name UNICOR.
FPI employs and provides skills training to
Federal inmates in diverse factory settings and contributes to the
safety and security of Bureau facilities by
keeping inmates constructively occupied.
The Prison Industries Act was adopted by ALEC's Criminal Justice Task Force, now known as the Public Safety and Elections Task Force,
at the Spring Task Force Summit on May 1, 2004, amended at the Annual
Meeting on July 29, 2004, and approved by the full ALEC Board of
Directors in August, 2004.
The victims of unethical human experiments and coerced research under National Socialism
In the past 30 years, the population of prisoners in the United States has expanded almost 5-fold, correctional facilities are
increasingly overcrowded, and more of the country's disadvantaged
populations—racial minorities, women, people with mental illness, and
people with communicable diseases such as HIV/AIDS, hepatitis C, and
tuberculosis—are under correctional supervision.
Because prisoners face restrictions on liberty and autonomy, have limited privacy, and often receive inadequate health care, they require specific protections when involved in research, particularly in today's correctional settings. Given these issues, the Department of Health and Human Services' Office for Human Research Protections commissioned the Institute of Medicine to review the ethical considerations regarding research involving prisoners.
The resulting analysis contained in this book, Ethical Considerations for Research Involving Prisoners, emphasizes five broad actions to provide prisoners involved in research with critically important protections:
• expand the definition of "prisoner";
• ensure universally and consistently applied standards of protection;
• shift from a category-based to a risk-benefit approach to research review;
• update the ethical framework to include collaborative responsibility; and
• enhance systematic oversight of research involving prisoners.
Because prisoners face restrictions on liberty and autonomy, have limited privacy, and often receive inadequate health care, they require specific protections when involved in research, particularly in today's correctional settings. Given these issues, the Department of Health and Human Services' Office for Human Research Protections commissioned the Institute of Medicine to review the ethical considerations regarding research involving prisoners.
The resulting analysis contained in this book, Ethical Considerations for Research Involving Prisoners, emphasizes five broad actions to provide prisoners involved in research with critically important protections:
• expand the definition of "prisoner";
• ensure universally and consistently applied standards of protection;
• shift from a category-based to a risk-benefit approach to research review;
• update the ethical framework to include collaborative responsibility; and
• enhance systematic oversight of research involving prisoners.
Cheaper than Chimpanzees: Expanding the Use of Prisoners in Medical Experiments
Humanizing Prisons with Animals: A Closer Look at "Cell Dogs" and Horse Programs in Correctional Institutions
Experimentation on Prisoners: Persistent Dilemmas in Rights and Regulations
How do you like that Angora and Kashmir now?
BioSteel was a trademark name for a high-strength fiber-based material made of the recombinant spider silk-like protein extracted from the milk of transgenic goats, made by Montreal-based company Nexia Biotechnologies, and later by the Randy Lewis lab of the University of Wyoming and Utah State University.[1]
It is reportedly 7-10 times as strong as steel if compared for the same
weight, and can stretch up to 20 times its unaltered size without
losing its strength properties. It also has very high resistance to
extreme temperatures, not losing any of its properties within −20 to 330
degrees Celsius (−4 to 626 degrees Fahrenheit).
The 13th Amendment left a loophole for prisoners to be forced to work without pay. Texas remains one of five states that exploits the carveout for state profit.
U.S. Government Legal Information: Shepardizing Cases
The 1970s saw some of the highest rates of inflation
in the United States in recent history, with interest rates rising in
turn to nearly 20%. Central bank policy, the abandonment of the gold
window, Keynesian economic policy, and market psychology all contributed
to this decade of high inflation
Labor strife, pressure on the Fed, a sharp rise in oil prices, but without stagflation and other key elements.
Where Your Wool Comes From
The eight Peruvian immigrants who work as shepherds on the S. Martinez ranch in Washington have a colossal job: keep about 4,000 animals safe from predators so their wool can be harvested in the spring for companies like Pendleton and Woolrich
Baa Baa Black SheepThere lived a black sheep in a nearby village. Every spring, he shaved his black wool and sold it to the villagers. The villagers made sweaters and socks from his black wool.
One day, the black sheep noticed that he had some more wool left. He thought, ‘It would be such a waste if nobody wants to buy the wool.’
That afternoon, an old man came over to his wooden shed to see him. He wanted one bag full of the black sheep’s wool. Then an old woman came over. She also wanted a bag full of wool. A short while later, a little boy arrived. He also wanted one bag full of wool.
Therefore, the black sheep prepared three bags full of wool for them. He was happy that all of his wool was sold off. Moral of the story :
We should be generous and helpful with what we have. We should be patient and not give up.
The Declaration of Helsinki (DoH, Finnish: Helsingin julistus, Swedish: Helsingforsdeklarationen) is a set of ethical principles regarding human experimentation developed for the medical community by the World Medical Association (WMA).[1] It is widely regarded as the cornerstone document on human research ethics.[1][2][3][4]
It is not a legally binding instrument under the international law, but instead draws its authority from the degree to which it has been codified in, or influenced, national or regional legislation and regulations.[5] Its role was described by a Brazilian forum in 2000 in these words "Even though the
Declaration of Helsinki is the responsibility of the World Medical Association, the document should be considered the property of all humanity".
A cashmere goat is a type of goat that produces cashmere wool, the goat's fine, soft, downy, winter undercoat, in commercial quality and quantity.[1] This undercoat grows as the day length shortens and is associated with an outer coat of coarse hair, which is present all the year and is called guard hair. Most common goat breeds, including dairy goats, grow this two-coated fleece.
The down is produced by secondary follicles, the guard hair by the primary follicles.[1]
In 1994, China had an estimated population of 123 million goats and is the largest producer of cashmere down. Local breeds are dominant. In the past decades, breeding programs have been started to develop productive breeds.[2] The cashmere goat is a fiber goat along with the Pygora goat, Nigora goat, and the Angora goat.
The goats take their name from their origin in the Himalayan region of Kashmir.
"male goat," cabrón is a Spanish slang word
roughly equivalent to the English bastard, badass, or dude, or even
cuckold, a man who's wife is cheating on him without him knowing about
it, depending on context. ... Cabrón begins as a “male goat,” with chiva as its female counterpart.
The billy goat is traditionally the image of the lust.
The reasons for the associations of goats with Satan vary.
Since 1856, the name Baphomet has been associated with a "Sabbatic Goat" image drawn by Eliphas Lévi
Further considerations of trade deals with China for Angora goats and Cashmere goats:
Faust is the protagonist of a classic German legend, based on the
historical Johann Georg Faust.
The erudite Faust is highly successful yet dissatisfied with his life,
which leads him to make a pact with the Devil at a crossroads,
exchanging his soul for unlimited knowledge and worldly pleasures.
If China Buys the farm today, they will get Sikie chickens and a Donkey from the Democratic convention:
The Silkie (sometimes spelled Silky) is a breed of chicken named for its atypically fluffy plumage, which is said to feel like silk
and satin. The breed has several other unusual qualities, such as black
skin and bones, blue earlobes, and five toes on each foot, whereas most
chickens only have four. They are often exhibited in poultry
shows, and appear in various colors. In addition to their distinctive
physical characteristics, Silkies are well known for their calm,
friendly temperament. It is among the most docile of poultry. Hens are
also exceptionally broody,
and care for young well. Though they are fair layers themselves, laying
only about three eggs a week, they are commonly used to hatch eggs from
other breeds and bird species due to their broody nature. Silkie
chickens are very easy to keep as pets. They are suitable for children,
but like any pet, should be handled with care.
Stockholm syndrome is a condition which causes hostages to develop a psychological alliance with their captors during captivity.[1] These alliances result from a bond formed between captor and captives during intimate time together, but they are generally considered irrational in light of the danger or risk endured by the victims. The FBI's Hostage Barricade Database System and Law Enforcement Bulletin indicate that roughly 8% of victims show evidence of Stockholm syndrome. [2][3] About ninety-six percent of victims involve suicide, domestic violence, and include people with previous relationships with the abuser.[4]
This term was first used by the media in 1973 when four hostages were taken during a bank robbery in Stockholm, Sweden. The hostages defended their captors after being released and would not agree to testify in court against them.[5] Stockholm syndrome is paradoxical because the sympathetic sentiments that captives feel towards their captors are the opposite of the fear and disdain which an onlooker might feel towards the captors.
The Thrilling Tale of How Robert Smalls Seized a Confederate Ship and Sailed it to Freedom
He risked his life to liberate his family and became a legend in the process
Some leaders do not appear to be mature enough for their position of authority.
Remember the movie Airplane?
The world's largest electric plane just took its first flight in the latest milestone for battery-powered passenger flights
Airplanes and helicopters flying into power lines is surprisingly common
There are multiple law firms that cater to injuries where helicopters or aircraft run into power lines.
Japan's 6th Generation Stealth Fighter Is Going To Blow The F-35 Away
Army's XVIII Airborne Corps Highlights Black D-Day Hero Denied Medal of Honor
The Department of Justice says prison labor is good for a company’s bottom line.
Barbadosed
Endemic warfare is a state of continual or frequent warfare, such as is found in some tribal societies (but is not limited to tribal societies).
Irish indentured servants
or crimping
Shanghaiing or crimping is the practice of kidnapping people to serve as sailors by coercive techniques such as trickery, intimidation, or violence. Those engaged in this form of kidnapping were known as crimps. The related term press gang refers specifically to impressment practices in Great Britain's Royal Navy.
Barracoon: The Story of the Last "Black Cargo" is a non-fiction work by Zora Neale Hurston. It is based on her interviews in 1927 with Cudjoe Lewis, the last living survivor of the Middle Passage.[1] The book failed to find a publisher at the time, in part because it was written in vernacular, and also in part because it described the involvement of other African people in the business of Atlantic slave trade
Genetically modified mosquitoes could be released in Florida and Texas beginning this summer – silver bullet or jumping the gun?
Prison labour is a billion-dollar industry, with uncertain returns for inmates
In Idaho, prisoners roast potatoes. In Kentucky, they sell cattle
Donkeys make acceptable guardians of sheep, goats and calves. ... Donkeys can protect against a single fox, coyote, roaming dog and possibly a bobcat. Donkeys who do attack a predator will be very aggressive, using their teeth and hooves. They may bray loudly.
The now-famous Democratic donkey was first associated with
Democrat Andrew Jackson's 1828 presidential campaign. His opponents
called him a jackass (a donkey), and Jackson decided to use the image of
the strong-willed animal on his campaign posters. Later, cartoonist
Thomas Nast used the Democratic donkey in newspaper cartoons and made
the symbol famous.
When you won, you divided the profits amongst you, and when you lost, you charged it to the bank. You tell me that if I take the deposits from the bank and annul its charter I shall ruin ten thousand families. That may be true, gentlemen, but that is your sin! - Andrew Jackson
When you won, you divided the profits amongst you, and when you lost, you charged it to the bank. You tell me that if I take the deposits from the bank and annul its charter I shall ruin ten thousand families. That may be true, gentlemen, but that is your sin! - Andrew Jackson
The verb Shepardizing refers to the process of consulting Shepard's to see if a case has been overturned, reaffirmed, questioned, or cited by later cases.
Protect Your Flock With Guard Donkeys
Kick up herd protection on your hobby farm with a guard donkey.
Metaphorically, the term "shepherd"
is used for God, especially in the Judeo-Christian tradition (e.g.
Psalm 23, Ezekiel 34), and in Christianity especially for Jesus, who
called himself the Good Shepherd. The Ancient Israelites were a pastoral people and there were many shepherds among them.
Donkey Kong is a series of video games featuring the adventures of a gorilla character called Donkey Kong, conceived by Shigeru Miyamoto in 1981
Donkey Kong is a series of video games featuring the adventures of a gorilla character called Donkey Kong, conceived by Shigeru Miyamoto in 1981
The 13th Amendment left a loophole for prisoners to be forced to work without pay. Texas remains one of five states that exploits the carveout for state profit.
U.S. Government Legal Information: Shepardizing Cases
The Prison Economy
Prison labor
Modern
medicine still depends on this animal’s blood to test for bacteria in
vaccines. And an alternative test requires further study.
Land of the Brave, Home of the Free:
Texas Correctional Industries
Texas PIE
Texas PIE
Prison Industry Enhancement Certification Program
Current PIE Certification Programs
| The Prison Industry Enhancement (PIE) Certification
Program is a partnership between the Texas Department of Criminal
Justice and a private company, which allows the company to employ
offenders that have volunteered to be a part of the program. The
offenders are paid by the private company and deductions are taken from
their wages for the offenders' taxes, room and board, family support
(incudes dependent/child support), restitution and a contribution is
made to a crime victims' fund. The PIE Certification Program was created by Congress in 1979 to encourage states and units of local government to establish employment opportunities for offenders in realistic working environments, pay them wages, and enable them to acquire marketable skills to increase their potential for successful rehabilitation and meaningful employment upon release. |
Current PIE Certification Programs
| Name | Henderson Controls, Inc. | OnShore Resources | |||
| Product | AC Parts & Heating Valves | Computer Boards & Wire Harnesses | |||
| Location | Lockhart Unit | Lockhart Unit | |||
Machine learning
The Fisher information is used in machine learning techniques such as elastic weight consolidation,[22] which reduces catastrophic forgetting in artificial neural networks.Fisher's exact test
By David Vincent Bell Hirsch
Sampling design
In the theory of finite population sampling, a sampling design specifies for every possible sample its probability of being drawn.
Matthew 5:43-48 New International Version (NIV)
Love for Enemies
Leviticus 19:9-18 English Standard Version (ESV)
Love Your Neighbor as Yourself
say awe
Variable Fusion: A New Adaptive Signal Regression Method
string theory, quantum knots, data threads and a braid group
Subfactor
What is Non-deterministic Polynomial Time?
In the theory of von Neumann algebras, a subfactor of a factor is a subalgebra that is a factor and contains. The theory of subfactors led to the discovery of the
Jones polynomial in knot theory.
A nondeterministic programming language is a language which can specify, at certain points in the program (called "choice points"), various alternatives for program flow. Unlike an if-then statement, the method of choice between these alternatives is not directly specified by the programmer; the program must decide at run time between the alternatives, via some general method applied to all choice points. A programmer specifies a limited number of alternatives, but the program must later choose between them. ("Choose" is, in fact, a typical name for the nondeterministic operator.) A hierarchy of choice points may be formed, with higher-level choices leading to branches that contain lower-level choices within them.
One method of choice is embodied in backtracking systems (such as Amb,[1] or unification in Prolog), in which some alternatives may "fail," causing the program to backtrack and try other alternatives. If all alternatives fail at a particular choice point, then an entire branch fails, and the program will backtrack further, to an older choice point. One complication is that, because any choice is tentative and may be remade, the system must be able to restore old program states by undoing side-effects caused by partially executing a branch that eventually failed.
Another method of choice is reinforcement learning, embodied in systems such as Alisp.[2] In such systems, rather than backtracking, the system keeps track of some measure of success and learns which choices often lead to success, and in which situations (both internal program state and environmental input may affect the choice). These systems are suitable for applications to robotics and other domains in which backtracking would involve attempting to undo actions performed in a dynamic environment, which may be difficult or impractical.
The palindromic density of an infinite word w over an alphabet A is defined to be zero if only finitely many prefixes are palindromes; otherwise, letting the palindromic prefixes be of lengths nk for k=1,2,... we define the density to be
Among aperiodic words, the largest possible palindromic density is achieved by the Fibonacci word, which has density 1/φ, where φ is the Golden ratio.
A palstar is a concatenation of palindromic strings, excluding the trivial one-letter palindromes – otherwise all strings would be palstars.
K
, is any of a group of four mesons distinguished by a quantum number called strangeness. In the quark model they are understood to be bound states of a strange quark (or antiquark) and an up or down antiquark (or quark).
Kaons have proved to be a copious source of information on the nature of fundamental interactions since their discovery in cosmic rays in 1947. They were essential in establishing the foundations of the Standard Model of particle physics, such as the quark model of hadrons and the theory of quark mixing (the latter was acknowledged by a Nobel Prize in Physics in 2008). Kaons have played a distinguished role in our understanding of fundamental conservation laws: CP violation, a phenomenon generating the observed matter–antimatter asymmetry of the universe, was discovered in the kaon system in 1964 (which was acknowledged by a Nobel Prize in 1980). Moreover, direct CP violation was discovered in the kaon decays in the early 2000s by the NA48 experiment at CERN and the KTeV experiment at Fermilab.
π
) is any of three subatomic particles:
π0,
π+, and
π−. Each pion consists of a quark and an antiquark and is therefore a meson. Pions are the lightest mesons and, more generally, the lightest hadrons. They are unstable, with the charged pions
π+ and
π− decaying after a mean lifetime of 26.033 nanoseconds (2.6033×10−8 seconds), and the neutral pion
π0 decaying after a much shorter lifetime of 84 attoseconds (8.4×10−17 seconds). Charged pions most often decay into muons and muon neutrinos, while neutral pions generally decay into gamma rays.
The exchange of virtual pions, along with vector, rho and omega mesons, provides an explanation for the residual strong force between nucleons. Pions are not produced in radioactive decay, but commonly are in high energy collisions between hadrons. Pions also result from some matter-antimatter annihilation events. All types of pions are also produced in natural processes when high energy cosmic ray protons and other hadronic cosmic ray components interact with matter in Earth's atmosphere. In 2013, the detection of characteristic gamma rays originating from the decay of neutral pions in two supernova remnants has shown that pions are produced copiously after supernovas, most probably in conjunction with production of high energy protons that are detected on Earth as cosmic rays.[1]
The concept of mesons as the carrier particles of the nuclear force was first proposed in 1935 by Hideki Yukawa. While the muon was first proposed to be this particle after its discovery in 1936, later work found that it did not participate in the strong nuclear interaction. The pions, which turned out to be examples of Yukawa's proposed mesons, were discovered later: the charged pions in 1947, and the neutral pion in 1950.
In physics, magnetic skyrmions (occasionally described as 'vortices,'[1] or 'vortex-like'[2] configurations) are quasiparticles[3] which have been predicted theoretically[1][4][5] and observed experimentally[6][7][8] in condensed matter systems. Skyrmions, named after British physicist Tony Hilton Royle Skyrme, can be formed in magnetic materials in their 'bulk' such as in MnSi,[7] or in magnetic thin films.[1][2][9] They can be achiral (Fig. 1 a), or chiral (Fig 1 b) in nature, and may exist both as dynamic excitations[3] or stable or metastable states.[6] Although the broad lines defining magnetic skyrmions have been established de facto, there exist a variety of interpretations with subtle differences.
Most descriptions include the notion of topology - a categorization of shapes and the way in which an object is laid out in space - using a continuous-field approximation as defined in micromagnetics.
Descriptions generally specify a non-zero, integer value of the topological index,[10] (not to be confused with the chemistry meaning of 'topological index'). This value is sometimes also referred to as the winding number,[11] the topological charge[10] (although it is unrelated to 'charge' in the electrical sense), the topological quantum number[12] (although it is unrelated to quantum mechanics or quantum mechanical phenomena, notwithstanding the quantization of the index values), or more loosely as the “skyrmion number.”[10]
In coding theory, a generator matrix is a matrix whose rows form a basis for a linear code. The codewords are all of the linear combinations of the rows of this matrix, that is, the linear code is the row space of its generator matrix.
Centroid
How do like them quantum biology analyte apple innovations with spintronics?
By David V. B. HirschNondeterministic algorithm
Nondeterministic Turing machine
A nondeterministic programming language is a language which can specify, at certain points in the program (called "choice points"), various alternatives for program flow. Unlike an if-then statement, the method of choice between these alternatives is not directly specified by the programmer; the program must decide at run time between the alternatives, via some general method applied to all choice points. A programmer specifies a limited number of alternatives, but the program must later choose between them. ("Choose" is, in fact, a typical name for the nondeterministic operator.) A hierarchy of choice points may be formed, with higher-level choices leading to branches that contain lower-level choices within them.
One method of choice is embodied in backtracking systems (such as Amb,[1] or unification in Prolog), in which some alternatives may "fail," causing the program to backtrack and try other alternatives. If all alternatives fail at a particular choice point, then an entire branch fails, and the program will backtrack further, to an older choice point. One complication is that, because any choice is tentative and may be remade, the system must be able to restore old program states by undoing side-effects caused by partially executing a branch that eventually failed.
Another method of choice is reinforcement learning, embodied in systems such as Alisp.[2] In such systems, rather than backtracking, the system keeps track of some measure of success and learns which choices often lead to success, and in which situations (both internal program state and environmental input may affect the choice). These systems are suitable for applications to robotics and other domains in which backtracking would involve attempting to undo actions performed in a dynamic environment, which may be difficult or impractical.
List of centroids
Medoid
k-means clustering
Quantum game theory
Would you be my Palstar?
It is possible to find the longest palindromic substring of a given input string in linear time.The palindromic density of an infinite word w over an alphabet A is defined to be zero if only finitely many prefixes are palindromes; otherwise, letting the palindromic prefixes be of lengths nk for k=1,2,... we define the density to be
Among aperiodic words, the largest possible palindromic density is achieved by the Fibonacci word, which has density 1/φ, where φ is the Golden ratio.
A palstar is a concatenation of palindromic strings, excluding the trivial one-letter palindromes – otherwise all strings would be palstars.
(game theory)
Sudoku solving algorithms
The cavity magnetron is a high-powered vacuum tube that generates microwaves using the interaction of a stream of electrons with a magnetic field while moving past a series of open metal cavities (cavity resonators). Electrons pass by the openings to these cavities and cause microwaves to oscillate within, similar to the way a whistle produces a tone when excited by an air stream blown past its opening. The frequency of the microwaves produced, the resonant frequency, is determined by the cavities' physical dimensions. Unlike other vacuum tubes such as a klystron or a traveling-wave tube (TWT), the magnetron cannot function as an amplifier in order to increase the intensity of an applied microwave signal; the magnetron serves solely as an oscillator, generating a microwave signal from direct current electricity supplied to the vacuum tube.
Finite von Neumann algebra
Cavity magnetron
Orbifold
The Magnetron
The microwave radiation of microwave ovens and some radar applications is produced by a device called a magnetron.
The magnetron is a high-powered vacuum tube that works as a self-excited microwave oscillator.
Crossed electron and magnetic fields are used in the magnetron to produce the high-power
output required in radar equipment
.
.
In the mathematical disciplines of topology, geometry, and geometric group theory, an orbifold (for "orbit-manifold") is a generalization of a manifold.
This Creepy Cosmic Radio Burst Repeats Every 157 Days. Where Is It Coming From?
We can't rule out aliens.
Out there in Hawaii
VLF transmitter Lualualei is a facility of the United States Navy near Lualualei, Hawaii transmitting orders to submerged submarines in the very low frequency (VLF) range.
Very low frequency or VLF is the ITU designation[1] for radio frequencies (RF) in the range of 3 to 30 kilohertz (kHz), corresponding to wavelengths from 100 to 10 kilometers, respectively. The band is also known as the myriameter band or myriameter wave as the wavelengths range from one to ten myriameters (an obsolete metric unit equal to 10 kilometers). Due to its limited bandwidth, audio (voice) transmission is highly impractical in this band, and therefore only low data rate coded signals are used. The VLF band is used for a few radio navigation services, government time radio stations (broadcasting time signals to set radio clocks)
and for secure military communication. Since VLF waves can penetrate
at least 40 meters (120 ft) into saltwater, they are used for military communication with submarines.
A klystron is a specialized linear-beam vacuum tube, invented in 1937 by American electrical engineers Russell and Sigurd Varian,[1] which is used as an amplifier for high radio frequencies, from UHF up into the microwave range. Low-power klystrons are used as oscillators in terrestrial microwave relay communications links, while high-power klystrons are used as output tubes in UHF television transmitters, satellite communication, radar transmitters, and to generate the drive power for modern particle accelerators.
Creation and Annihilation of Skyrmions in the Frustrated Magnets with Competing Exchange Interactions
Meanwhile, Carl Spackler, a somewhat unhinged groundskeeper who lives in the maintenance building, hunts a gopher that is damaging the course. Caddyshack
Kaon
In particle physics, a kaon /ˈkeɪ.ɒn/, also called a K meson and denotedK
, is any of a group of four mesons distinguished by a quantum number called strangeness. In the quark model they are understood to be bound states of a strange quark (or antiquark) and an up or down antiquark (or quark).
Kaons have proved to be a copious source of information on the nature of fundamental interactions since their discovery in cosmic rays in 1947. They were essential in establishing the foundations of the Standard Model of particle physics, such as the quark model of hadrons and the theory of quark mixing (the latter was acknowledged by a Nobel Prize in Physics in 2008). Kaons have played a distinguished role in our understanding of fundamental conservation laws: CP violation, a phenomenon generating the observed matter–antimatter asymmetry of the universe, was discovered in the kaon system in 1964 (which was acknowledged by a Nobel Prize in 1980). Moreover, direct CP violation was discovered in the kaon decays in the early 2000s by the NA48 experiment at CERN and the KTeV experiment at Fermilab.
Pion
In particle physics, a pion (or a pi meson, denoted with the Greek letter pi:π
) is any of three subatomic particles:
π0,
π+, and
π−. Each pion consists of a quark and an antiquark and is therefore a meson. Pions are the lightest mesons and, more generally, the lightest hadrons. They are unstable, with the charged pions
π+ and
π− decaying after a mean lifetime of 26.033 nanoseconds (2.6033×10−8 seconds), and the neutral pion
π0 decaying after a much shorter lifetime of 84 attoseconds (8.4×10−17 seconds). Charged pions most often decay into muons and muon neutrinos, while neutral pions generally decay into gamma rays.
The exchange of virtual pions, along with vector, rho and omega mesons, provides an explanation for the residual strong force between nucleons. Pions are not produced in radioactive decay, but commonly are in high energy collisions between hadrons. Pions also result from some matter-antimatter annihilation events. All types of pions are also produced in natural processes when high energy cosmic ray protons and other hadronic cosmic ray components interact with matter in Earth's atmosphere. In 2013, the detection of characteristic gamma rays originating from the decay of neutral pions in two supernova remnants has shown that pions are produced copiously after supernovas, most probably in conjunction with production of high energy protons that are detected on Earth as cosmic rays.[1]
The concept of mesons as the carrier particles of the nuclear force was first proposed in 1935 by Hideki Yukawa. While the muon was first proposed to be this particle after its discovery in 1936, later work found that it did not participate in the strong nuclear interaction. The pions, which turned out to be examples of Yukawa's proposed mesons, were discovered later: the charged pions in 1947, and the neutral pion in 1950.
Skyrmion
In particle theory, the skyrmion is a topologically stable field
configuration of a certain class of non-linear sigma models. It was
originally proposed as a model of the nucleon by Tony Skyrme in 1962
In physics, magnetic skyrmions (occasionally described as 'vortices,'[1] or 'vortex-like'[2] configurations) are quasiparticles[3] which have been predicted theoretically[1][4][5] and observed experimentally[6][7][8] in condensed matter systems. Skyrmions, named after British physicist Tony Hilton Royle Skyrme, can be formed in magnetic materials in their 'bulk' such as in MnSi,[7] or in magnetic thin films.[1][2][9] They can be achiral (Fig. 1 a), or chiral (Fig 1 b) in nature, and may exist both as dynamic excitations[3] or stable or metastable states.[6] Although the broad lines defining magnetic skyrmions have been established de facto, there exist a variety of interpretations with subtle differences.
Most descriptions include the notion of topology - a categorization of shapes and the way in which an object is laid out in space - using a continuous-field approximation as defined in micromagnetics.
Descriptions generally specify a non-zero, integer value of the topological index,[10] (not to be confused with the chemistry meaning of 'topological index'). This value is sometimes also referred to as the winding number,[11] the topological charge[10] (although it is unrelated to 'charge' in the electrical sense), the topological quantum number[12] (although it is unrelated to quantum mechanics or quantum mechanical phenomena, notwithstanding the quantization of the index values), or more loosely as the “skyrmion number.”[10]
and....
What does a neutral kaon decay into?
These particles decay into pions by. The quark mixing which leads to these combinations involves the exchange of two W bosons. The neutral kaons are important historically for their part in advancing our understanding of quark processes.
The radio spectrum is the part of the electromagnetic spectrum with frequencies from 30 hertz to 300 GHz. Electromagnetic waves in this frequency range, called radio waves, are widely used in modern technology, particularly in telecommunication. To prevent interference between different users, the generation and transmission of radio waves is strictly regulated by national laws, coordinated by an international body, the International Telecommunication Union (ITU)
Almost complex manifold
For Bluetooth WiFi innovations:
Ultra high frequency (UHF) is the ITU designation for radio frequencies in the range between 300 megahertz (MHz) and 3 gigahertz (GHz), also known as the decimetre band as the wavelengths range from one meter to one tenth of a meter (one decimeter). Radio waves with frequencies above the UHF band fall into the super-high frequency (SHF) or microwave frequency range. Lower frequency signals fall into the VHF (very high frequency) or lower bands. UHF radio waves propagate mainly by line of sight;
they are blocked by hills and large buildings although the transmission
through building walls is strong enough for indoor reception. They are
used for television broadcasting, cell phones, satellite communication including GPS, personal radio services including Wi-Fi and Bluetooth, walkie-talkies, cordless phones, and numerous other applications.
UHF is more practical for hardware and software innovations for commercial use. Another consideration is Skip or Skywave:
In radio communication, skywave or skip refers to the propagation of radio waves reflected or refracted back toward Earth from the ionosphere, an electrically charged layer of the upper atmosphere. Since it is not limited by the curvature of the Earth, skywave propagation can be used to communicate beyond the horizon, at intercontinental distances. It is mostly used in the shortwave frequency bands.
Servo Motors and Control with Arduino Platforms
The ancient Peruvian mystery solved from space
Groundwater Law
A look at the ancient rule of capture and the modern Accommodation Doctrine.
By Justin Hodge and Graham TaylorThe Flaming Lips Perform in Giant Bubbles on Colbert
COMMUNITY
CLIMATE PLAN
Zoom is a reference platform that features TI's OMAP 3430/3630 processors.
Texas Instruments Embraces Next-Gen Mobile Processor
The OMAP 3430 was built on a 65nm process (like Qualcomm's Snapdragon),
while the 3630 is a 45nm shrink (like Apple's A4). Architecturally the
two SoCs are very similar. They both use a standard ARM Cortex A8 CPU
paired with an Imagination Technologies PowerVR SGX 530 GPU. The two
SoCs fit in the same size package (12mm x 12mm BGA) and are ball
compatible. If a customer wanted to, it could simply drop in a 3630 into
an existing 3430 design with minimal engineering efforts.
- ARM (5 members)
- ARM Development Boards (42 members)
- ARM processors (37 members)
all object code is halfword aligned
Problem with alignment of variable in memory
Markov property
Projection, Hat, influence matrix maps the vector of response values (dependent variable values) to the vector of fitted values (or predicted values). It describes the influence each response value has on each fitted value.In coding theory, a generator matrix is a matrix whose rows form a basis for a linear code. The codewords are all of the linear combinations of the rows of this matrix, that is, the linear code is the row space of its generator matrix.
- Causal Markov condition
- Chapman–Kolmogorov equation
- Hysteresis
- The most common type of compiler-compiler is more precisely called a parser generator
Strange Attractors: Creating Patterns in Chaos
by Julien C. Sprott
An attractor is a set of states (points in the phase space), invariant under the dynamics, towards which neighboring states in a given basin of attraction asymptotically approach in the course of dynamic evolution. ... Trajectories within a strange attractor appear to skip around randomly.
Resistor
Real radical
Radical of an ideal
Jacobson radical
Nilradical of a ring
En (Lie algebra)
Root lattice
The root lattice of En has determinant 9 − n, and can be constructed as the lattice of vectors in the unimodular Lorentzian lattice Zn,1 that are orthogonal to the vector (1,1,1,1,...,1|3) of norm n × 12 − 32 = n − 9.E7½
Main article: E7½
Landsberg and Manivel extended the definition of En for integer n to include the case n = 7½. They did this in order to fill the "hole" in dimension formulae for representations of the En series which was observed by Cvitanovic, Deligne, Cohen and de Man. E7½ has dimension 190, but is not a simple Lie algebra: it contains a 57 dimensional Heisenberg algebra as its nilradical.Lotka–Volterra equations
Two species
Competitive Lotka–Volterra equations
Predator-Prey Models
John 1:1 is the first verse in the
opening chapter of the Gospel of John. In the Douay–Rheims, King James,
New International, and other versions of the Bible, the verse reads: In the beginning was the Word, and the Word was with God, and the Word was God.
(SBIR Innovation with Chaos topology quantum biology)
Predator - Prey Dynamics - Rats and Snakes (Lotka Volterra Simulation)
Predator - Prey Dynamics - Rats and Snakes (Lotka Volterra Simulation)
Navy Invests in New Mine Warfare Technology (UPDATED)
Fibonacci word fractal
hang on somebody's words/every word
Logistic map
Topological quantum computer
A topological quantum computer is a theoretical quantum computer that employs two-dimensional quasiparticles called anyons, whose world lines pass around one another to form braids in a three-dimensional spacetime (i.e., one temporal plus two spatial dimensions). These braids form the logic gates that make up the computer. The advantage of a quantum computer based on quantum braids over using trapped quantum particles is that the former is much more stable. Small, cumulative perturbations can cause quantum states to decohere and introduce errors in the computation, but such small perturbations do not change the braids' topological properties. This is like the effort required to cut a string and reattach the ends to form a different braid, as opposed to a ball (representing an ordinary quantum particle in four-dimensional spacetime) bumping into a wall. Alexei Kitaev proposed topological quantum computation in 1997. While the elements of a topological quantum computer originate in a purely mathematical realm, experiments in fractional quantum Hall systems indicate these elements may be created in the real world using semiconductors made of gallium arsenide at a temperature of near absolute zero and subjected to strong magnetic fields.
"Fishers of men" is a phrase used in the gospels to describe the
mandate given by Jesus to his first disciples. Two brother fishermen,
Simon called Peter and Andrew, were casting a net into the Sea of
Galilee
Machine learning
The Fisher information is used in machine learning techniques such as elastic weight consolidation,[22] which reduces catastrophic forgetting in artificial neural networks.Möbius strip
Graduate Student Solves Decades-Old Conway Knot Problem
It took Lisa Piccirillo less than a week to answer a long-standing question about a strange knot discovered over half a century ago by the legendary John Conway.
Pi bonds (π bonds) are covalent chemical bonds
where two lobes of an orbital on one atom overlap two lobes of an
orbital on another atom and this overlap occurs laterally. ... The same
plane is also a nodal plane for the molecular orbital of the pi bond.
List of geodesic polyhedra and Goldberg polyhedra
Tutte polynomial
A chiral molecule or
ion exists in two stereoisomers that are mirror images of each other,
called enantiomers; they are often distinguished as either
"right-handed" or "left-handed" by their absolute configuration or some
other criterion.
Almost surely
In probability theory, an event is said to happen almost surely (sometimes abbreviated as a.s.) if it happens with probability 1 (or Lebesgue measure 1).[1][2]
In other words, the set of possible exceptions may be non-empty, but it
has probability 0. The concept is essentially analogous to the concept
of "almost everywhere" in measure theory.
In probability experiments on a finite sample space, there is often no difference between almost surely and surely (since having a probability of 1 often entails including all the sample points).
However, this distinction becomes important when the sample space is an infinite set,[3] because an infinite set can have non-empty subsets of probability 0.
Some examples of the use of this concept include the strong and uniform versions of the law of large numbers, and the continuity of the paths of Brownian motion.
In probability experiments on a finite sample space, there is often no difference between almost surely and surely (since having a probability of 1 often entails including all the sample points).
However, this distinction becomes important when the sample space is an infinite set,[3] because an infinite set can have non-empty subsets of probability 0.
Some examples of the use of this concept include the strong and uniform versions of the law of large numbers, and the continuity of the paths of Brownian motion.
B-spline
In the mathematical subfield of numerical analysis, a B-spline, or basis spline, is a spline function that has minimal support with respect to a given degree, smoothness, and domain partition. Any spline function of given degree can be expressed as a linear combination of B-splines of that degree. Cardinal B-splines have knots that are equidistant from each other. B-splines can be used for curve-fitting and numerical differentiation of experimental data.
Annihilator (ring theory)
- Annihilator (ring theory)
- In mathematics, specifically module theory, annihilators are a concept that formalizes torsionand generalizes torsion and orthogonal complement.
In mathematics, specifically module theory, the annihilator of a set is a concept generalizing torsion and orthogonality.
Set (abstract data type)
In mathematics, the braid group on n strands, also known as the Artin braid group,[1] is the group whose elements are equivalence classes of n-braids (e.g. under ambient isotopy), and whose group operation is composition of braids (see § Introduction). Example applications of braid groups include knot theory, where any knot may be represented as the closure of certain braids (a result known as Alexander's theorem); in mathematical physics where Artin's canonical presentation of the braid group corresponds to the Yang–Baxter equation (see § Basic properties); and in monodromy invariants of algebraic geometry
string theory, quantum knots, data threads and a braid group
Subfactor
In the theory of von Neumann algebras, a subfactor of a factor is a subalgebra that is a factor and contains... The theory of subfactors led to the discovery of the
Jones polynomial in knot theory.
Theory of Games and Economic Behavior, published in 1944 by Princeton University Press, is a book by mathematician John von Neumann
and economist Oskar Morgenstern which is considered the groundbreaking
text that created the interdisciplinary research field of game theory.
Hash table
The idea of hashing is to distribute the entries (key/value pairs) across an array of buckets.
If all keys are known ahead of time, a perfect hash function can be used to create a perfect hash table that has no collisions.
Key statistics
St Hubert's Key
"I will give you the keys of
the kingdom of heaven; whatever you bind on earth will be bound in
heaven, and whatever you loose on earth will be loosed in heaven."
Orthoptera
Orthoptera is an order of insects that comprises the grasshoppers, locusts and crickets, including closely related insects such as the katydids and wetas. The order is subdivided into two suborders: Caelifera – grasshoppers, locusts and close relatives; and Ensifera – crickets and close relatives.More than 20,000 species are distributed worldwide.[1] The insects in the order have incomplete metamorphosis, and produce sound (known as a "stridulation") by rubbing their wings against each other or their legs, the wings or legs containing rows of corrugated bumps. The tympanum or ear is located in the front tibia in crickets, mole crickets, and katydids, and on the first abdominal segment in the grasshoppers and locusts.[2] These organisms use vibrations to locate other individuals.
Grasshoppers and other orthopterans are able to fold their wings (i.e. they are members of Neoptera), and they are frequently grouped with similar "Orthopteroid" insect orders.
Hemiptera. The Hemiptera /hɛˈmɪptərə/ or true bugs are an order of insects comprising some 50,000 to 80,000 species of groups such as the cicadas,
aphids, planthoppers, leafhoppers, and shield bugs. They range in size
from 1 mm (0.04 in) to around 15 cm (6 in), and share a common
arrangement of sucking mouthparts.
In mathematical logic and logic programming, a Horn clause is a logical formula of a particular rule-like form which gives it useful properties for use in logic programming, formal specification, and model theory. Horn clauses are named for the logician Alfred Horn, who first pointed out their significance in 1951.[1]
A Knot Polynomial Invariant for Analysis of Topology of RNA Stems and Protein Disulfide Bonds
Ornithology is a branch of zoology that concerns the study of
birds. Several aspects of ornithology differ from related disciplines,
due partly to the high visibility and the aesthetic appeal of birds
Little Herds: a company sharing the joy of edible insects
Could edible insects be the answer to feeding a
global population expected to hit 9 billion by 2050? New Food caught up
with Robert Nathan Allen, founder of Little Herds, to find ou
The evolution of extreme altruism and inequality in insect societies
Evolution: Modeling evolutionary transitions in social insects
호박벌과 친구가 되는 과정
(the process of making friends with a carpenter bee)
We should really talk to entomologists about these social conventions.
Relief of Douglas MacArthur
How the Korean War Almost Went Nuclear
In 1950, Harry Truman had to decide whether to use B-29s to drop atomic bombs.
Deep Learning Theory Review: An Optimal Control and Dynamical Systems Perspective
Attempts from different disciplines to provide a fundamental understanding of deep learning have advanced rapidly in recent years, yet a unified framework remains relatively limited. In this article, we provide one possible way to align existing branches of deep learning theory through the lens of dynamical system and optimal control. By viewing deep neural networks as discrete-time nonlinear dynamical systems, we can analyze how information propagates through layers using mean field theory. When optimization algorithms are further recast as controllers, the ultimate goal of training processes can be formulated as an optimal control problem. In addition, we can reveal convergence and generalization properties by studying the stochastic dynamics of optimization algorithms. This viewpoint features a wide range of theoretical study from information bottleneck to statistical physics. It also provides a principled way for hyper-parameter tuning when optimal control theory is introduced. Our framework fits nicely with supervised learning and can be extended to other learning problems, such as Bayesian learning, adversarial training, and specific forms of meta learning, without efforts. The review aims to shed lights on the importance of dynamics and optimal control when developing deep learning theory.
| Comments: | Under Submission |
| Subjects: | Machine Learning (cs.LG); Systems and Control (eess.SY); Machine Learning (stat.ML) |
https://arxiv.org/abs/1908.
In quantum mechanics, bra–ket notation is a standard notation for describing quantum states.
lambda, map and filter in Python
In mathematics, a sequence of nested intervals is understood as a collection of sets of real numbers.
The elementary or first-order theory of Heyting algebras is undecidable.
It remains open whether the universal Horn theory of Heyting algebras,
or word problem, is decidable. À propos of the word problem it is known
that Heyting algebras are not locally finite (no Heyting algebra
generated by a finite nonempty set is finite), in contrast to Boolean
algebras which are locally finite and whose word problem is decidable.
It is unknown whether free complete Heyting algebras exist except in the
case of a single generator where the free Heyting algebra on one
generator is trivially completable by adjoining a new top.
Street-Fighting Mathematics
The Art of Educated Guessing and Opportunistic Problem Solving
By Sanjoy Mahajan
The Art of Educated Guessing and Opportunistic Problem Solving
By Sanjoy Mahajan
Programmers, Machine Learners or Learners
Interests include:
Machine Learning in Genomics - Current Efforts and Future Applications
as for
Composite Knot
is a knot that is not a prime knot. Schubert (1949) showed that every knot can be uniquely decomposed (up to the order in which the decomposition is performed) as a knot sum of a class of knots known as prime knots, which cannot themselves be further decomposed (Hoste et al. 1998).
In mathematics, in particular knot theory, the Conway knot (or Conway's knot) is a particular knot with 11 crossings, named after John Horton Conway.[1] It is related by mutation to the Kinoshita–Terasaka knot.[2]
The long-unsolved issue of the sliceness of the Conway knot was only resolved in 2020.[3]
The long-unsolved issue of the sliceness of the Conway knot was only resolved in 2020.[3]
A Bézier curve (/ˈbɛz.i.eɪ/ BEH-zee-ay)[1] is a parametric curve used in computer graphics and related fields.[2] The curve, which is related to the Bernstein polynomial, is named after Pierre Bézier, who used it in the 1960s for designing curves for the bodywork of Renault cars.[3] Other uses include the design of computer fonts and animation.[3] Bézier curves can be combined to form a Bézier spline, or generalized to higher dimensions to form Bézier surfaces.[3] The Bézier triangle is a special case of the latter.
A checksum is a small-sized datum derived from a block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage.
It is usually applied to an installation file after it is received
from the download server. By themselves, checksums are often used to
verify data integrity but are not relied upon to verify data authenticity.
The rank-nullity theorem is a fundamental theorem in linear
algebra which relates the dimensions of a linear map's kernel and image
with the dimension of its domain.
In linear algebra, the Cayley–Hamilton theorem (named after the mathematicians Arthur Cayley and William Rowan Hamilton) states that every square matrix over a commutative ring (such as the real or complex field) satisfies its own characteristic equation.
In the mathematical fields of geometry and linear algebra, a principal axis is a certain line in a Euclidean space associated with an ellipsoid or hyperboloid, generalizing the major and minor axes of an ellipse or hyperbola. The principal axis theorem states that the principal axes are perpendicular, and gives a constructive procedure for finding them.
Mathematically, the principal axis theorem is a generalization of the method of completing the square from elementary algebra. In linear algebra and functional analysis, the principal axis theorem is a geometrical counterpart of the spectral theorem. It has applications to the statistics of principal components analysis and the singular value decomposition. In physics, the theorem is fundamental to the study of angular momentum.
Mathematically, the principal axis theorem is a generalization of the method of completing the square from elementary algebra. In linear algebra and functional analysis, the principal axis theorem is a geometrical counterpart of the spectral theorem. It has applications to the statistics of principal components analysis and the singular value decomposition. In physics, the theorem is fundamental to the study of angular momentum.
Goppa code
In mathematics, an algebraic geometric code (AG-code), otherwise known as a Goppa code, is a general type of linear code constructed by using an algebraic curve over a finite field. Such codes were introduced by Valerii Denisovich Goppa. In particular cases, they can have interesting extremal properties. They should not be confused with binary Goppa codes that are used, for instance, in the McEliece cryptosystem.
A complete walk through using Bayesian optimization for automated hyperparameter tuning in Python
In coding theory, a cyclic code is a block code, where the circular shifts of each codeword gives another word that belongs to the code. They are error-correcting codes that have algebraic properties that are convenient for efficient error detection and correction.
Banana Bond
In organic chemistry, a bent bond, also known as a banana bond, is a type of covalent chemical bond with a geometry somewhat reminiscent of a banana. The term itself is a general representation of electron density or configuration resembling a similar "bent" structure within small ring molecules, such as cyclopropane (C3H6) or as a representation of double or triple bonds within a compound that is an alternative to the sigma and pi bond model.
Banana Pi Bond data slice, hold the Octonions!
Chiral Packing? Chiral molecules lead to macroscopically chiral phases of matter.
What?
Some of your Hyperon might as well Lepton some tangent spin structure energy!
Is that not Good enough of a scheme for you?
In numerical analysis and computational fluid dynamics, Godunov's scheme is a conservative numerical scheme, suggested by S. K. Godunov in 1959, for solving partial differential equations. One can think of this method as a conservative finite-volume method which solves exact, or approximate Riemann problems at each inter-cell boundary.
New findings are fueling an old suspicion that fundamental particles and forces spring from strange eight-part numbers called “octonions.”
Pick's Theorem is a useful method for determining the area of any polygon whose vertices are points on a lattice, a regularly spaced array of points.
Chiral Packing? Chiral molecules lead to macroscopically chiral phases of matter.
What?
Some of your Hyperon might as well Lepton some tangent spin structure energy!
Is that not Good enough of a scheme for you?
In numerical analysis and computational fluid dynamics, Godunov's scheme is a conservative numerical scheme, suggested by S. K. Godunov in 1959, for solving partial differential equations. One can think of this method as a conservative finite-volume method which solves exact, or approximate Riemann problems at each inter-cell boundary.
New findings are fueling an old suspicion that fundamental particles and forces spring from strange eight-part numbers called “octonions.”
Pick's Theorem is a useful method for determining the area of any polygon whose vertices are points on a lattice, a regularly spaced array of points.
Spinor bundle
In mathematics, a Green's function is the impulse response of an inhomogeneous linear differential equation defined on a domain, with specified initial conditions or boundary conditions.Molecular orbital theory. In chemistry, molecular orbital (MO) theory is a method for describing the electronic structure of molecules. Electrons are not assigned to individual bonds between atoms, but are treated as moving under the influence of the nuclei in the whole molecule.
Valence Bond Model vs. Molecular Orbital Theory
In chemistry, molecular orbital (MO) theory is a method for describing the electronic structure of molecules. Electrons are not assigned to individual bonds between atoms, but are treated as moving under the influence of the nuclei in the whole molecule. The spatial and energetic properties of electrons are described by quantum mechanics as atomic or molecular orbitals that contain these electrons. While atomic orbitals contain electrons ascribed to a single atom, molecular orbitals surround two or more atoms in a molecule and contain valence electrons between atoms. Molecular orbital theory, which was proposed in the early twentieth century, revolutionized the study of bonding by approximating the states of bonded electrons—the molecular orbitals—as linear combinations of atomic orbitals (LCAO). These approximations are now made by applying the density functional theory (DFT) or Hartree–Fock (HF) models to the Schrödinger equation.
Skyrmion
In mathematics, spin geometry is the area of differential geometry and topology where objects like spin manifolds and Dirac operators, and the various associated index theorems have come to play a fundamental role both in mathematics and in mathematical physics.An important generalisation is the theory of symplectic Dirac operators in symplectic spin geometry and symplectic topology, which have become important fields of mathematical research.
Spintronics
Spintronics (a portmanteau meaning spin transport electronics), also known as spin electronics, is the study of the intrinsic spin of the electron and its associated magnetic moment, in addition to its fundamental electronic charge, in solid-state devices. The field of spintronics concerns spin-charge coupling in metallic systems; the analogous effects in insulators fall into the field of multiferroics.
Spintronics fundamentally differs from traditional electronics in
that, in addition to charge state, electron spins are exploited as a
further degree of freedom, with implications in the efficiency of data
storage and transfer. Spintronic systems are most often realised in dilute magnetic semiconductors (DMS) and Heusler alloys and are of particular interest in the field of quantum computing and neuromorphic computing.
Symplectic geometry
Symplectic geometry is a branch of differential geometry and differential topology that studies symplectic manifolds; that is, differentiable manifolds equipped with a closed, nondegenerate 2-form. Symplectic geometry has its origins in the Hamiltonian formulation of classical mechanics where the phase space of certain classical systems takes on the structure of a symplectic manifold.Quantum Monte Carlo
Moment map
Silixa acoustic sensors
(innovations)
WiMAX MIMO refers to the use of Multiple-input multiple-output communications (MIMO) technology on WiMAX, which is the technology brand name for the implementation of the standard IEEE 802.16.
In radio, multiple-input and multiple-output, or MIMO (/ˈmaɪmoʊ, ˈmiːmoʊ/),
is a method for multiplying the capacity of a radio link using multiple
transmission and receiving antennas to exploit multipath propagation.
February 11, 2019
Smart antennas (also known as adaptive array antennas, digital antenna arrays, multiple antennas and, recently, MIMO) are antenna arrays with smart signal processing algorithms used to identify spatial signal signatures such as the direction of arrival
(DOA) of the signal, and use them to calculate beamforming vectors
which are used to track and locate the antenna beam on the
mobile/target. Smart antennas should not be confused with reconfigurable
antennas, which have similar capabilities but are single element
antennas and not antenna arrays.
A loop antenna is a radio antenna consisting of a loop or coil of wire, tubing, or other electrical conductor
usually fed by a balanced source or feeding a balanced load. Within
this physical description there are two distinct antenna types.
Geometric mechanics
Understanding Electromagnetic Radiation! | ICT #5
Chaos theory
Total order
The endless knot or eternal knot (Sanskrit: śrīvatsa; simplified Chinese: 盘长结; traditional Chinese: 盤長結; pinyin: pánzhǎng jié; Tibetan དཔལ་བེའུ། dpal be'u; Mongolian Улзии) is a symbolic knot and one of the Eight Auspicious Symbols. It is an important symbol in both Jainism and Buddhism. It is an important cultural marker in places significantly influenced by Tibetan Buddhism such as Tibet, Mongolia, Tuva, Kalmykia, and Buryatia. It is also found in Celtic and Chinese symbolism.
The seamless garment philosophy holds that issues such as abortion, capital punishment, militarism, euthanasia, social injustice, and economic injustice all demand a consistent application of moral principles that value the sacredness of human life. "The protection of life", said Egan, "is a seamless garment.
How to build an antiracist world
Ibram X. Kendi
The Ashtamangala is a sacred suite of Eight Auspicious Signs endemic to a number of religions such as Hinduism, Jainism, and Buddhism. The symbols or "symbolic attributes" (Tibetan: ཕྱག་མཚན་, THL: chaktsen) are yidam and teaching tools. Not only do these attributes (or energetic signatures) point to qualities of enlightened mindstream, but they are the investiture that ornaments these enlightened "qualities" (Sanskrit: guṇa; Tibetan: ཡོན་ཏན་, THL: yönten). Many cultural enumerations and variations of the Ashtamangala are extant.
The seamless garment philosophy holds that issues such as abortion, capital punishment, militarism, euthanasia, social injustice, and economic injustice all demand a consistent application of moral principles that value the sacredness of human life. "The protection of life", said Egan, "is a seamless garment.
How to build an antiracist world
Ibram X. Kendi
The Ashtamangala is a sacred suite of Eight Auspicious Signs endemic to a number of religions such as Hinduism, Jainism, and Buddhism. The symbols or "symbolic attributes" (Tibetan: ཕྱག་མཚན་, THL: chaktsen) are yidam and teaching tools. Not only do these attributes (or energetic signatures) point to qualities of enlightened mindstream, but they are the investiture that ornaments these enlightened "qualities" (Sanskrit: guṇa; Tibetan: ཡོན་ཏན་, THL: yönten). Many cultural enumerations and variations of the Ashtamangala are extant.
Ashtamangala: first row (left to right): parasol, pair of golden fish, conch; second row: treasure vase, lotus; Last row: infinite knot, victory banner and wheel.
In Jainism it is one of the eight auspicious items, an asthamangala, however found only in the Svetambara sect. It is often found marking the chests of the
The name "Borromean rings" comes from their use in the coat of arms of the aristocratic Borromeo family in Northern Italy. The link itself is much older and has appeared in the form of the valknut on Norse image stones dating back to the 7th century.
The Borromean rings as a symbol of the Christian Trinity, from a 13th-century manuscript.
The Borromean rings have been used in different contexts to indicate
strength in unity, e.g., in religion or art. In particular, some have
used the design to symbolize the Trinity. The psychoanalyst Jacques Lacan
famously found inspiration in the Borromean rings as a model for his
topology of human subjectivity, with each ring representing a
fundamental Lacanian component of reality (the "real", the "imaginary",
and the "symbolic").
The valknut is a symbol consisting of three interlocked triangles. It appears on a variety of objects from the archaeological record of the ancient Germanic peoples. The term valknut
is derived from the modern era and the term or terms used to referred
to the symbol during its historical employment is unknown.
The valknut as trefoil knot or triquetra (unicursal)
- As Borromean rings on the Stora Hammars I stone
The triquetra (/traɪˈkwɛtrə/; from the Latin adjective triquetrus "three-cornered")
is a triangular figure composed of three interlaced arcs, or (equivalently) three overlapping vesicae piscis lens shapes.
Solomon's knot (Latin: sigillum Salomonis, literally 'Solomon's seal') is a traditional decorative motif used since ancient times, and found in many cultures. Despite the name, it is classified as a link, and is not a true knot according to the definitions of mathematical knot theory.
Cathode and Anode waves
I enjoy the art work as well philosophy of Walter Russell.
He suggests
Cathode waves wind the cosmic clock centripetally Anode transverse waves unwind it centrifugally
A node is a point along a standing wave where the wave has minimum amplitude. For instance, in a vibrating guitar string, the ends of the string are nodes. By changing the position of the end node through frets, the guitarist changes the effective length of the vibrating string and thereby the note played. The opposite of a node is an anti-node, a point where the amplitude of the standing wave is at maximum. These occur midway between the nodes
Mathematics
- Vertex (graph theory), a vertex in a mathematical graph
- Node (autonomous system), behaviour for an ordinary differential equation near a critical point
- Singular point of an algebraic variety, a type of singular point of a curve
Physics
- Node (physics), a point along a standing wave where the wave has minimal amplitude
Biology
- Lymph node, an immune system organ used to store white blood cells
- Node of Ranvier, periodic gaps in the insulating myelin sheaths of myelinated axons
- Sinoatrial node and atrioventricular node, specialized tissues in the heart responsible for initiating and coordinating the heartbeat
- Primitive node is the organizer tissue for gastrulation in vertebrates.
- The place on a plant stem where a leaf is attached
- In Cladistics, a shared ancestor (also see Clade)
Commercial chitosan is derived from the shells of shrimp and other sea crustaceans
Chitin nanofibers are extracted from
crustacean waste and mushrooms for possible development of products in
tissue engineering, medicine, and industry.
Chitin
The Gordian Knot is a legend of Phrygian Gordium associated with Alexander the Great. It is often used as a metaphor
for an intractable problem (untying an impossibly tangled knot) solved
easily by finding an approach to the problem that renders the perceived
constraints of the problem moot ("cutting the Gordian knot"):
Turn him to any cause of policy,
The Gordian Knot of it he will unloose,
Familiar as his garter— Shakespeare, Henry V, Act 1 Scene 1. 45–47
Topochemistry
Christoph A. Schalley*
Antibody injections could fight COVID-19 infections – an infectious disease expert explains the prospects
In organic chemistry, a bent bond, also known as a banana bond, is a type of covalent chemical bond with a geometry somewhat reminiscent of a banana. The term itself is a general representation of electron density or configuration resembling a similar "bent" structure within small ring molecules, such as cyclopropane (C3H6) or as a representation of double or triple bonds within a compound that is an alternative to the sigma and pi bond model.
The Godfather of Sexist Pseudoscience
Mimosa pudica[2] (from Latin: pudica "shy, bashful or shrinking"; also called sensitive plant, sleepy plant, action plant,[3] Dormilones, touch-me-not, shameplant, zombie plant, or shy plant)
These plants have a consideration for a
Mimosa pudica[2] (from Latin: pudica "shy, bashful or shrinking"; also called sensitive plant, sleepy plant, action plant,[3] Dormilones, touch-me-not, shameplant, zombie plant, or shy plant) is a creeping annual or perennial flowering plant of the pea/legume family Fabaceae and Magnoliopsida
taxon, often grown for its curiosity value: the compound leaves fold
inward and droop when touched or shaken, defending themselves from harm,
and re-open a few minutes later.[4]
Insect-damaged Arabidopsis Moves Like Wounded Mimosa pudica
NIMHD
has an active funding opportunity that calls for applications proposing
simulation modeling and systems science to address health disparities.
For your reference, please
see:
In knot theory, the stevedore knot is one of three prime knots with crossing number six, the others being the 62 knot and the 63 knot. The stevedore knot is listed as the 61 knot in the Alexander–Briggs notation, and it can also be described as a twist knot with four twists, or as the (5,−1,−1) pretzel knot.
The mathematical stevedore knot is named after the common stevedore knot, which is often used as a stopper at the end of a rope. The mathematical version of the knot can be obtained from the common version by joining together the two loose ends of the rope, forming a knotted loop.
The stevedore knot is invertible but not amphichiral. Its Alexander polynomial is its Conway polynomial and its Jones polynomial
The Alexander polynomial and Conway polynomial are the same as those for the knot 946, but the Jones polynomials for these two knots are different.[2] Because the Alexander polynomial is not monic, the stevedore knot is not fibered.
The stevedore knot is a ribbon knot, and is therefore also a slice knot.
The stevedore knot is a hyperbolic knot, with its complement having a volume of approximately 3.16396.
One can see that the Hamburger moment problem is intimately related to orthogonal polynomials on the real line. The Gram–Schmidt procedure gives a basis of orthogonal polynomials in which the operator: has a tridiagonal Jacobi matrix representation. This in turn leads to a tridiagonal model of positive Hankel kernels.
as a kissing stem-loop, or kissing stem loop interaction, is formed in RNA when two bases between two hairpin loops pair.
In mathematics, the Alexander polynomial is a knot invariant which assigns a polynomial with integer coefficients to each knot type. James Waddell Alexander II discovered this, the first knot polynomial, in 1923. In 1969, John Conway showed a version of this polynomial, now called the Alexander–Conway polynomial, could be computed using a skein relation, although its significance was not realized until the discovery of the Jones polynomial
in 1984. Soon after Conway's reworking of the Alexander polynomial, it
was realized that a similar skein relation was exhibited in Alexander's
paper on his polynomial.[1]
In mathematical logic and logic programming, a Horn clause is a logical formula of a particular rule-like form which gives it useful properties for use in logic programming, formal specification, and model theory. Horn clauses are named for the logician Alfred Horn, who first pointed out their significance in 1951.[1]
The Spanish word Topo translates into English as Mole.
Topo Chico is sparkling mineral water sourced and bottled in Monterrey, Mexico since 1895.
In espionage jargon, a mole (also called a "penetration agent", "deep cover agent", or "sleeper agent") is a long-term spy (espionage agent) who is recruited before having access to secret intelligence, subsequently managing to get into the target organization.
Boy's surface
Boy's surface is discussed (and illustrated) in Jean-Pierre Petit's Topo the world.[1]
Red Rover
Red rover (also known as forcing the city gates and octopus tag) is a game played primarily by children on playgrounds. This 19th-century children's group game (requiring 10+ players)[1] is thought to have originated in the United Kingdom and then spread to Australia, Canada and the United States.
In other languages
In Russia and other former USSR countries, this game has been known as "Ali Baba", in Hungary as "Adj, király, katonát!" (King, give us a soldier!)[3] and in Serbia as "Јелечкиње, барјачкиње" (jelečkinje, barjačkinje, i.e., city crier and flag bearer).[4]In Romania, the game is known as "Țara, țara vrem ostași" (Country, country we want soldiers).[5]
In the Czech Republic, the game is known as "Král vysílá své vojsko" (The king sends out his army), with the difference that each team chooses which of its members will attempt to break the other team's line, rather than sending the member called by the other team.[6]
The Polish phrase that will help you through tough times
In Poland, the concept of 'Jakoś to będzie' is acting without worrying about the consequences. It’s reaching for the impossible. It’s taking risks, and not being afraid.
What is a foreign policy actor?
Common governmental actors or institutions which make foreign policy
decisions include: the head of state (such as a president) or head of
government (such as a prime minister), cabinet, or minister. ... Other
departments may also have a role in implementing foreign policy, such as departments for: trade, defence, and aid.
Philip Pullella
The role of policy actors and contextual factors in policy agenda setting and formulation: maternal fee exemption policies in Ghana over four and a half decades
Adam's Bridge,[a] also known as Rama's Bridge or Rama Setu[b] is a chain of limestone shoals, between Pamban Island, also known as Rameswaram Island, off the south-eastern coast of Tamil Nadu, India, and Mannar Island, off the north-western coast of Sri Lanka. Geological evidence suggests that this bridge is a former land connection between India and Sri LankaIn the Hindu epic Ramayana, Nala (Sanskrit: नल, IAST: nala, lit. lotus),the son of Vishwakarma is the vanara, who is credited as the engineer of the Rama Setu, a bridge across the ocean between Rameswaram (India) and Lanka, identified with modern-day Sri Lanka, so forces of the god Rama can pass over to Lanka.[1][2] The bridge is also known as Nala Setu, the bridge of Nala.[3] Sometimes, another vanara called Nila is also credited as the builder of the bridge. Nala is described as the architect of the vanaras. Nala is also described to have fought in the battle between Rama and Ravana, the king of Lanka.
The endless knot or eternal knot (Sanskrit: śrīvatsa; simplified Chinese: 盘长结; traditional Chinese: 盤長結; pinyin: pánzhǎng jié; Tibetan དཔལ་བེའུ། dpal be'u; Mongolian Улзии) is a symbolic knot and one of the Eight Auspicious Symbols. It is an important symbol in both Jainism and Buddhism. It is an important cultural marker in places significantly influenced by Tibetan Buddhism such as Tibet, Mongolia, Tuva, Kalmykia, and Buryatia. It is also found in Celtic and Chinese symbolism.
The seamless garment philosophy holds that issues such as abortion, capital punishment, militarism, euthanasia, social injustice, and economic injustice all demand a consistent application of moral principles that value the sacredness of human life. "The protection of life", said Egan, "is a seamless garment.
The Ashtamangala is a sacred suite of Eight Auspicious Signs endemic to a number of religions such as Hinduism, Jainism, and Buddhism. The symbols or "symbolic attributes" (Tibetan: ཕྱག་མཚན་, THL: chaktsen) are yidam and teaching tools. Not only do these attributes (or energetic signatures) point to qualities of enlightened mindstream, but they are the investiture that ornaments these enlightened "qualities" (Sanskrit: guṇa; Tibetan: ཡོན་ཏན་, THL: yönten). Many cultural enumerations and variations of the Ashtamangala are extant.
Ashtamangala: first row (left to right): parasol, pair of golden fish,
conch; second row: treasure vase, lotus; Last row: infinite knot,
victory banner and wheel.
In Jainism it is one of the eight auspicious items, an asthamangala, however found only in the Svetambara sect.
The Missouri Mule. The Missouri Mule. On May 31, 1995, Governor Mel Carnahan signed a bill designating the Missouri Mule as the official state animal. The mule is a hybrid animal, the offspring of a mare (female horse) and a jack (male donkey).
While much of the state's history is tied to the mighty rivers that flow through it, the "Show Me State" got its nickname because of the devotion of its people to simple common sense. In 1899, Rep. Willard D. Vandiver said, "Frothy eloquence neither convinces nor satisfies me. I'm from Missouri. You've got to show me."
What is the state animal of Missouri?
Chanting the Third Eye
Making the everyday sacred through the beauty of Yantra practice
Posted on July 15, 2015 by Yoga for Diabetes
Missouri mule
The Missouri Mule. The Missouri Mule. On May 31, 1995, Governor Mel Carnahan signed a bill designating the Missouri Mule as the official state animal. The mule is a hybrid animal, the offspring of a mare (female horse) and a jack (male donkey).
Army Close to Awarding New Contract for Robotic Mule to Carry Gear for Grunts
Democratic Plank and Platform
His son, my great grandfather Doctor Price Bell from Indian Territory (Oklahoma)
How did Missouri get the nickname the Show Me State?
While much of the state's history is tied to the mighty rivers that flow through it, the "Show Me State" got its nickname because of the devotion of its people to simple common sense. In 1899, Rep. Willard D. Vandiver said, "Frothy eloquence neither convinces nor satisfies me. I'm from Missouri. You've got to show me."
How Do I Pitch to MTV?
By Ty Wright ; Updated September 15, 2017
Animal Missouri mule 1995
A lot for a Frog, Texas to hop to like that Warner Brothers Frog
Michigan J. Frog
as
Quantum Leaps, Long Assumed to Be Instantaneous, Take Time
The Whitewater controversy, Whitewater scandal, or simply Whitewater, was an American political controversy during the 1990s. It began with
an investigation into the real estate investments of Bill and Hillary
Clinton and their associates, Jim McDougal and Susan McDougal, in the Whitewater Development Corporation.
Miami Will Be Underwater Soon. Its Drinking Water Could Go First
The city has another serious water problem.
2020 elections and those Dam Failures... something to write home about...
Trump misstates Michigan mail-in ballot policy, threatens federal funding
It is the latest escalation from the president, who is adamantly opposed to mail-in elections.Flower Drop Tips: Reasons Why Healthy Blooms Fall Off
Tie a yellow ribbon round the old oak tree
Disney Music - Lava (Official Lyric Video from "Lava")
And as far as Flying Squirrels go...
The statement "There are no atheists in foxholes" is an aphorism used to argue that in times of extreme stress or fear, such as during war ("in foxholes"), all people will believe in, or hope for, a higher power (and there are therefore no atheists).[1]
Squirrels tend to split the nuts neatly in half. Common dormice leave a smooth, round hole in the side of the nut, with tooth marks running around the inside of the hole. Wood mice leave tooth marks on the surface of the nut and across the edge of the hole. The hole may be either circular or ragged in shape.
The term "eye of a needle" is used as a metaphor for a very narrow
opening. It occurs several times throughout the Talmud. The New
Testament quotes Jesus as saying that "it is easier for a camel to go
through the eye of a needle than for a rich man to enter the kingdom of
God".
What size hole can a squirrel get through?
A flying squirrel can fit through a hole as small as a nickel coin. A gray squirrel can fit through a hole as small as a quarter. Holes can be sealed with wood, metal or 1/2 inch wire mesh.
Flying squirrel can fit through a hole as small as a nickel
Note: The black squirrel occurs as a melanistic subgroup of both the eastern gray squirrel (Sciurus carolinensis) and the fox squirrel (S. niger) Although black and gray squirrels look different, they belong to the same species, the eastern gray squirrel (Sciurus carolinensis). Black coats are just one of the many possible eastern gray's coat colors. Fox squirrels, although usually reddish-brown, can also have black coats.
Note: The black squirrel occurs as a melanistic subgroup of both the eastern gray squirrel (Sciurus carolinensis) and the fox squirrel (S. niger) Although black and gray squirrels look different, they belong to the same species, the eastern gray squirrel (Sciurus carolinensis). Black coats are just one of the many possible eastern gray's coat colors. Fox squirrels, although usually reddish-brown, can also have black coats.
What is the purpose of a hobo nickel?
The hobo nickel is a sculptural art form involving the creative modification of small-denomination coins, essentially resulting in miniature bas reliefs. The US nickel coin was favored because of its size, thickness and relative softness.
A gray squirrel can fit through a hole as small as a quarter.
The hobo nickel is a sculptural art form involving the creative modification of small-denomination coins, essentially resulting in miniature bas reliefs. The US nickel coin was favored because of its size, thickness and relative softness. However, the term hobo nickel is generic, as carvings have been made from many different denominations.
Geologic Setting and Geochemistry of Thermal Water and Geothermal Assessment, Trans-Pecos Texas and Adjacent Mexico
A commodity pool operator is a salesman for a fund that invests in commodities futures. A CPO may work for a hedge fund or investment fund that takes positions in commodities. CPOs must register with the Commodities Futures Trading Commission
A Commodity pool operator (CPO) is an individual or organization that solicits or receives funds to use in the operation of a commodity pool, syndicate, investment trust, or other similar fund, specifically for trading in commodity interests. Such interests include commodity futures, swaps, options and/or leverage transactions.[1][2] A commodity pool may refer to funds that trade in commodities and can include hedge funds. A CPO may make trading decisions for a fund or the fund can be managed by one or more independent commodity trading advisors.[1] The definition of CPO may apply to investment advisors for hedge funds and private funds including mutual funds and exchange-traded funds in certain cases.[3] CPOs are generally regulated by the United States federal government through the Commodity Futures Trading Commission and National Futures Association.
What was Roosevelt's quarantine speech?
The Quarantine Speech was given by U.S. President Franklin D. Roosevelt on October 5, 1937 in Chicago (on the occasion of the dedication of the bridge between north and south outer Lake Shore Drive)
Posted on October 30, 2007 by Institute for PR
Generosity is a sign of intelligence, and givers are the rising tide that lifts all boats.
The George Foster Peabody Awards (or simply Peabody Awards or the Peabodys[1]) program, named for the American businessman and philanthropist George Peabody,
honor the most powerful, enlightening, and invigorating stories in
television, radio, and online media. Programs are recognized in seven
categories: news, entertainment, documentaries, children's programming,
education, interactive programming, and public service
Can Animals Count?
Wasps Can Recognize Faces
Social species relies on recognition to keep the peace, study suggests.
How many eyes does a wasp have?
three
“Ocellus” means “simple eye”. “Ocelli” is the plural of “ocellus". Wasps, for instance have three and they're arranged in a triangle between their two compound eyes.
Simon & Schuster's Guide to Insects pg. 33
"
Some wasps appeared to be able to count!
A fixed number of caterpillars were placed in the pot, although they
fell through the bottom and noe remained inside. As soon as the Pot was
full a specific number of caterpillars had been dropped in - the pot was
capped and away flew the female wasp blissfully unaware of the futility
of her efforts. Other Species that could not "count" went on trying to
fill the pot until they died of exhaustion, ran out of eggs, or lost
interest because the initial stimulus ran off"
Potter Wasp Stunsand Shoves CaterpillarInto PotTutorial: Qubit characterization with the HDAWG |
|
Among
the most important and most frequently performed type of measurement in
quantum technology applications is qubit characterization. To learn how
to use your HDAWG multi-channel Arbitrary Waveform Generator
to do just that, take a look at our new tutorial in the HDAWG User
Manual. The tutorial discusses how to use existing and new features such
as oscillator phase control to perform Rabi oscillation, lifetime and
coherence time measurements, as well as spin-locking experiments.
| |
Sensor characterization and control |
|
When
a sensor's behavior is altered by a change in the surrounding
environment, the characterization of the sensor's response is a crucial
step for its development. In this blog post, Kıvanç Esat looks at the
fastest ways to use time- and frequency-domain tools to characterize
sensing devices. Importantly, he shows how to set up feedback loops for
sensor control without the need for time-consuming and expensive
application-specific integrated circuitry (ASIC) development.
| |
You have to be real observant to notice differences from Mud daubers and Potter Wasps as well Mason Wasps and others:
Mud dauber
Eye-Opener: Why Do Pupils Dilate in Response to Emotional States?
It has been said that the eyes are windows to the soul. Research has at least shown that the apertures of our eyes offer a glimpse into the mindNew Model of Evolution Finally Reveals How Cooperation Evolves
By treating evolution as a thermodynamic process, theorists have solved one the great problems in biology.
Emerging Technology from the arXiv
Vespidae
It takes many lessons to raise awareness with observations.
So, insects taste, smell, touch and communicate in part through antennae, thus allowing them
to gather information about food sources, potential mates (pheromones),
enemies, dangerous substances (e. g. a poisonous plant), nesting places
and migratory routes (as in the case of the monarch butterfly).
Cicadas' Cycles Control Their Predators
By Virginia MorellDec. 14, 2012 , 5:05 PM
Aposematism is the advertising by an animal to potential predators that it is not worth attacking or eating. This unprofitability may consist of any defences which make the prey difficult to kill and eat, such as toxicity, venom, foul taste or smell, sharp spines, or aggressive nature.
Holometabolism, also called complete metamorphosis, is a form of insect development which includes four life stages: egg, larva, pupa, and imago or adult. Holometabolism is a synapomorphic trait of all insects in the superorder Endopterygota.
Immature stages of holometabolous insects are very different from the
mature stage. In some species the holometabolous life cycle prevents
larvae from competing with adults because they inhabit different ecological niches.
The morphology and behavior of each stage are adapted for different
activities. For example, larval traits maximize feeding, growth, and
development, while adult traits enable dispersal, mating, and egg
laying. Some species of holometabolous insects protect and feed their
offspring. Other insect developmental strategies include ametabolism and hemimetabolism.
Ecdysone is a steroidal prohormone of the major insect molting hormone 20-hydroxyecdysone, which is secreted from the prothoracic glands. Insect molting hormones are generally called ecdysteroids.
Mimics Parade
Parthenogenesis (/ˌpɑːrθɪnoʊˈdʒɛnɪsɪs, -θɪnə-/;[1][2] from the Greek παρθένος, parthenos, 'virgin' + γένεσις, genesis, 'creation'[3]) is a natural form of asexual reproduction in which growth and development of embryos occur without fertilization by sperm. In animals, parthenogenesis means development of an embryo from an unfertilized egg cell. In plants parthenogenesis is a component process of apomixis.
Parthenogenesis occurs naturally in some plants, some invertebrate animal species (including nematodes, water fleas, some scorpions, aphids, some mites, some bees, some Phasmatodea and parasitic wasps) and a few vertebrates (such as some fish,[4] amphibians, reptiles[5][6] and very rarely birds[7]). This type of reproduction has been induced artificially in a few species including fish and amphibians.[8]
Normal egg cells form after meiosis and are haploid, with half as many chromosomes as their mother's body cells. Haploid individuals, however, are usually non-viable, and parthenogenetic offspring usually have the diploid chromosome number. Depending on the mechanism involved in restoring the diploid number of chromosomes, parthenogenetic offspring may have anywhere between all and half of the mother's alleles. The offspring having all of the mother's genetic material are called full clones and those having only half are called half clones. Full clones are usually formed without meiosis. If meiosis occurs, the offspring will get only a fraction of the mother's alleles since crossing over of DNA takes place during meiosis, creating variation.
Parthenogenetic offspring in species that use either the XY or the X0 sex-determination system have two X chromosomes and are female. In species that use the ZW sex-determination system, they have either two Z chromosomes (male) or two W chromosomes (mostly non-viable but rarely a female), or they could have one Z and one W chromosome (female).
Kamakiri is Japanese for a Mantis,
sprangle means spread out
Definition of sprangle
intransitive verb
: to spread out in different directions : branch out : ramify, straggle
streams sprangle over the countryside
transitive verb
1
: to cause to sprangle : diffuse
2
: to rough up the feathers of (an arrow) as by injury or carelessness
Seeing a praying mantis can be considered to be good luck or bad, depending on your culture. Because of the 'praying' hands, some Christians say that the praying mantis represents spiritualism or piety, and if found in your home, may mean that angels are watching over you.
Geothermal Energy Is a Key Building Block of a Clean Energy Future
NREL to Study Geothermal Deep Direct-Use in East Texas Power Plants
July 14, 2017
How do like them quantum biology analyte apple innovations with spintronics?
By David V. B. Hirsch
Saint-Venant's theorem
In solid mechanics, it is common to analyze the properties of beams with constant cross section. Saint-Venant's theorem states that the simply connected cross section with maximal torsional rigidity is a circle.
Simple shear is a deformation
in which parallel planes in a material remain parallel and maintain a
constant distance, while translating relative to each other.
A shear stress, often denoted by τ (Greek: tau), is the component of stress coplanar with a material cross section. Shear stress arises from the force vector component parallel to the cross section of the material. Normal stress, on the other hand, arises from the force vector component perpendicular to the material cross section on which it acts.
Shear stress arises from shear forces, which are pairs of equal and opposing forces acting on opposite sides of an object.
In mathematics, a shear matrix or transvection is an elementary matrix that represents the addition of a multiple of one row or column to another. Such a matrix may be derived by taking the identity matrix and replacing one of the zero elements with a non-zero value.
In the field of solid mechanics, torsion is the twisting of an object due to an applied torque. Torsion is expressed in either the Pascal (Pa), an SI unit for newtons per square metre, or in pounds per square inch (psi) while torque is expressed in newton metres (N·m) or foot-pound force (ft·lbf). In sections perpendicular to the torque axis, the resultant shear stress in this section is perpendicular to the radius.
Shear stress arises from shear forces, which are pairs of equal and opposing forces acting on opposite sides of an object.
In mathematics, a shear matrix or transvection is an elementary matrix that represents the addition of a multiple of one row or column to another. Such a matrix may be derived by taking the identity matrix and replacing one of the zero elements with a non-zero value.
In the field of solid mechanics, torsion is the twisting of an object due to an applied torque. Torsion is expressed in either the Pascal (Pa), an SI unit for newtons per square metre, or in pounds per square inch (psi) while torque is expressed in newton metres (N·m) or foot-pound force (ft·lbf). In sections perpendicular to the torque axis, the resultant shear stress in this section is perpendicular to the radius.
Torsion spring
A torsion spring is a spring that works by twisting its end along its axis; that is, a flexible elastic object that stores mechanical energy when it is twisted. When it is twisted, it exerts a torque in the opposite direction, proportional to the amount (angle) it is twisted. There are various types:- A torsion bar is a straight bar of metal or rubber that is subjected to twisting (shear stress) about its axis by torque applied at its ends.
- A more delicate form used in sensitive instruments, called a torsion fiber consists of a fiber of silk, glass, or quartz under tension, that is twisted about its axis.
- A helical torsion spring, is a metal rod or wire in the shape of a helix (coil) that is subjected to twisting about the axis of the coil by sideways forces (bending moments) applied to its ends, twisting the coil tighter.
Second moment of area
The 2nd moment of area, or second area moment and also known as the area moment of inertia, is a geometrical property of an area which reflects how its points are distributed with regard to an arbitrary axis. The second moment of area is typically denoted with either an (for an axis that lies in the plane) or with a
(for an axis that lies in the plane) or with a  (for an axis perpendicular to the plane). In both cases, it is calculated with a multiple integral over the object in question. Its dimension is L (length) to the fourth power. Its unit of dimension when working with the International System of Units is meters to the fourth power, m4, or inches to the fourth power, in4, when working in the Imperial System of Units.
(for an axis perpendicular to the plane). In both cases, it is calculated with a multiple integral over the object in question. Its dimension is L (length) to the fourth power. Its unit of dimension when working with the International System of Units is meters to the fourth power, m4, or inches to the fourth power, in4, when working in the Imperial System of Units.
In structural engineering, the second moment of area of a beam is an important property used in the calculation of the beam's deflection and the calculation of stress caused by a moment applied to the beam. In order to maximize the second moment of area, a large fraction of the cross-sectional area of an I-beam is located at the maximum possible distance from the centroid of the I-beam's cross-section. The planar second moment of area provides insight into a beam's resistance to bending due to an applied moment, force, or distributed load perpendicular to its neutral axis, as a function of its shape. The polar second moment of area provides insight into a beam's resistance to torsional deflection, due to an applied moment parallel to its cross-section, as a function of its shape.
NUWC-NPT
ReprintReport
11,907
1 March2009
How Private Equity Is Ruining American Health Care
Investors
have been buying up doctor’s offices, cutting costs, and, critics
say, putting pressure on physicians in ways that hurt patients. The
pandemic could make things even worse.
Books
Why Birds Do What They Do
The more humans understand about their behavior, the more inaccessible their world seems.
Jean-Henri Fabre
The Australian Bassian thrush farts toward the ground, with the noxious smell helping to unearth worms and other insect prey. Bassian thrush are known to dislodge their prey out of pile of leaves by disturbing the leaf litter. The birds move quietly, but often pause, to listen for the movements of the insects. They also disturb worm prey by farting, which provokes the worms to move. The Bassian thrush releases gas to scare worms out of hiding.
What do the feathers in a headdress represent?
War bonnets (also called warbonnets or headdresses) are feathered
headgear traditionally worn by male leaders of the American Plains
Indians Nations who have earned a place of great respect in their tribe.
Originally they were sometimes worn into battle, but they are now
primarily used for ceremonial occasions.
Consider 1922
Secretary of the Treasury and
1924: James Brown MP (made a privy counsellor before serving again in 1930) within the context of
Black Tuesday: October 29, 1929
On Monday, however, the storm broke anew, and the market went into free fall. Black Monday was followed by Black Tuesday (October 29, 1929), in which stock prices collapsed completely and 16,410,030 shares were traded on the New York Stock Exchange in a single day.
Jean-Henri Fabre
25 Things You Might Not Know About the Birds in Your Backyard
BY Jake Rossen
The Australian Bassian thrush farts toward the ground, with the noxious smell helping to unearth worms and other insect prey. Bassian thrush are known to dislodge their prey out of pile of leaves by disturbing the leaf litter. The birds move quietly, but often pause, to listen for the movements of the insects. They also disturb worm prey by farting, which provokes the worms to move. The Bassian thrush releases gas to scare worms out of hiding.
‘Freedom Gas,’ the Next American Export
By
Alkane
Got Gas? It Could Mean You've Got Healthy Gut Microbes
Annals of TechnologyThe Cicada’s Love Affair With Prime Numbers
By Patrick Di Justo
May 13, 2013What do the feathers in a headdress represent?
The headdress
is a well-known symbol of strength and bravery in Native American
culture. It is believed that the Sioux were of the first tribes to wear
the feather headdress. ... Historically, headdresses have been worn by the most powerful and influential members among a tribe and were not typically made in one day.
Who wears a feathered headdress and why?
The Meeting at Jekyll Island
November 20, 1910–November 30, 1910
A secret gathering at a secluded island off the coast of Georgia in 1910 laid the foundations for the Federal Reserve System.Jekyll Island Club
Slavery and the American University
The Untouchables
Why it’s getting harder to stop multinational corporations.
Lord High Commissioner to the General Assembly of the Church of Scotland
List of Lords High Commissioner
...
- 1921–1922: The Duke of Sutherland
- 1923: The Lord Elphinstone
- 1924: James Brown MP (made a privy counsellor before serving again in 1930)
Black Tuesday: October 29, 1929
On Monday, however, the storm broke anew, and the market went into free fall. Black Monday was followed by Black Tuesday (October 29, 1929), in which stock prices collapsed completely and 16,410,030 shares were traded on the New York Stock Exchange in a single day.
Wall Street Crash of 1929
little bird told me. Fig. a way of indicating that you do not want to reveal who told
you something. (Sometimes used playfully, when you think that the
person you are addressing knows or can guess who was the source of your
information.)
The Smith Mundt Act of 2012 made propaganda legal in the United States.
Richard Bowditch "Dick" Wigglesworth (April 25, 1891 – October 22, 1960) was an American football player and coach and United States Representative from Massachusetts. He was born in Boston. He graduated from Milton Academy in 1908.
He attended Harvard University, where he was the starting quarterback for the Harvard Crimson football team from 1909 to 1911.
Wigglesworth graduated from Harvard in 1912, and from Harvard Law School in 1916. He also served as a graduate coach of the Harvard football team starting in 1912.[1] He was assistant private secretary to the Governor General of the Philippine Islands. He was admitted to the bar and commenced practice in Boston.
During World War I he served overseas as captain, Battery E, and as commanding officer, First Battalion, Three Hundred and Third Field Artillery, Seventy-sixth Division, 1917-1919. He served as legal adviser to the Assistant Secretary of the Treasury in charge of foreign loans and railway payments, and secretary of the World War Debt Commission 1922-1924. He was assistant to the agent general for reparation payments, Berlin, Germany 1924-1927. He was general counsel and Paris representative for organizations created under the Dawes plan in 1927 and 1928.
Wigglesworth was elected as a Republican to the Seventieth Congress to fill the vacancy caused by the death of Louis A. Frothingham. He was reelected to the Seventy-first and to the fourteen succeeding Congresses and served from November 6, 1928, until his resignation November 13, 1958.
Wigglesworth voted in favor of the Civil Rights Act of 1957.[2] He served as United States Ambassador to Canada from December 15, 1958, until his death in Boston on October 22, 1960.[3] His interment was in Arlington National Cemetery.
Wigglesworth married Florence Joyes Booth in 1931, and they had three daughters, Ann, Mary and Jane.[4][5]
Meaning of wiggle room in English. the freedom or opportunity to do something, or to change your mind and do something differently if that is what is needed: We need to leave ourselves some wiggle room when we're negotiating the deal.
The Smith Mundt Act of 2012 made propaganda legal in the United States.
Richard Bowditch "Dick" Wigglesworth (April 25, 1891 – October 22, 1960) was an American football player and coach and United States Representative from Massachusetts. He was born in Boston. He graduated from Milton Academy in 1908.
He attended Harvard University, where he was the starting quarterback for the Harvard Crimson football team from 1909 to 1911.
Wigglesworth graduated from Harvard in 1912, and from Harvard Law School in 1916. He also served as a graduate coach of the Harvard football team starting in 1912.[1] He was assistant private secretary to the Governor General of the Philippine Islands. He was admitted to the bar and commenced practice in Boston.
During World War I he served overseas as captain, Battery E, and as commanding officer, First Battalion, Three Hundred and Third Field Artillery, Seventy-sixth Division, 1917-1919. He served as legal adviser to the Assistant Secretary of the Treasury in charge of foreign loans and railway payments, and secretary of the World War Debt Commission 1922-1924. He was assistant to the agent general for reparation payments, Berlin, Germany 1924-1927. He was general counsel and Paris representative for organizations created under the Dawes plan in 1927 and 1928.
Wigglesworth was elected as a Republican to the Seventieth Congress to fill the vacancy caused by the death of Louis A. Frothingham. He was reelected to the Seventy-first and to the fourteen succeeding Congresses and served from November 6, 1928, until his resignation November 13, 1958.
Wigglesworth voted in favor of the Civil Rights Act of 1957.[2] He served as United States Ambassador to Canada from December 15, 1958, until his death in Boston on October 22, 1960.[3] His interment was in Arlington National Cemetery.
Wigglesworth married Florence Joyes Booth in 1931, and they had three daughters, Ann, Mary and Jane.[4][5]
Meaning of wiggle room in English. the freedom or opportunity to do something, or to change your mind and do something differently if that is what is needed: We need to leave ourselves some wiggle room when we're negotiating the deal.
Both the Tango and Waltz
have several variations to them. One of the more popular dances of the
1920s, which was still seen on dance floors into the 1950s, was the Lindy Hop, which later became known as the Jitterbug. The Lindy Hop was the original swing dance.
A schrödinbug is a bug that manifests only after someone reading source code or using the program in an unusual way notices that it never should have worked in the first place, at which point the program promptly stops working for everybody until fixed. The Jargon File adds: "Though... this sounds impossible, it happens; some programs have harbored latent schrödinbugs for years."
Balfour Declaration
The Balfour Declaration was a public statement issued by the British government in 1917 during the First World War announcing support for the establishment of a "national home for the Jewish people" in Palestine, then an Ottoman region with a small minority Jewish population. The declaration was contained in a letter dated 2 November 1917 from the United Kingdom's Foreign Secretary Arthur Balfour to Lord Rothschild, a leader of the British Jewish community, for transmission to the Zionist Federation of Great Britain and Ireland. The text of the declaration was published in the press on
9 November 1917.
The Apprentice
2004 ‧ Reality ‧ 15 seasons
First episode date: January 8, 2004
barnstorm
verb
1.: to tour through rural districts staging usually theatrical performances
2 : to travel from place to place making brief stops (as in a political campaign or a promotional tour)
3 : to
pilot one's airplane in sightseeing flights with passengers or in
exhibition stunts in an unscheduled course especially in rural districts
The use of a special purse or burse to hold the Great Seal of the Realm, the Lord Chancellor's symbol of Office, can be traced as far back as the end of the 13th Century. The purse is solemnly carried before the Lord Chancellor in procession on State occasions.[1]
It no longer contains the Great Seal which now reposes at the Palace of Westminster;[2] it is however used by the Lord Chancellor to convey the signed copy of the Queen's Speech printed on vellum, from the Queen's Robing Room to the steps of the Throne in the Chamber of the House of Lords, at every State Opening of Parliament.[3]
The Purse presently in use is made from crimson velvet and lavishly embellished with the Royal Arms and Emblems.
Richard Bowditch "Dick" Wigglesworth served as legal adviser to the Assistant Secretary of the Treasury in charge of foreign loans and railway payments, and secretary of the World War Debt Commission 1922-1924 and 1924: James Brown MP (made a privy counsellor before serving again in 1930)
Palace of Westminster
The Purse bearer is an official in the Royal Households of the United Kingdom, and based in the Ministry of Justice.The use of a special purse or burse to hold the Great Seal of the Realm, the Lord Chancellor's symbol of Office, can be traced as far back as the end of the 13th Century. The purse is solemnly carried before the Lord Chancellor in procession on State occasions.[1]
It no longer contains the Great Seal which now reposes at the Palace of Westminster;[2] it is however used by the Lord Chancellor to convey the signed copy of the Queen's Speech printed on vellum, from the Queen's Robing Room to the steps of the Throne in the Chamber of the House of Lords, at every State Opening of Parliament.[3]
The Purse presently in use is made from crimson velvet and lavishly embellished with the Royal Arms and Emblems.
Queen's Robing Room
Indeed rulers of Germany, Russia and England are all related! Robbing room more likely...
Princess Alexandra and Princess Dagmar, who pulled off the dynastic
coup of the 19th century by marrying the heirs to both the British and
Russian thrones. Following the invasion of their native Denmark by
Prussia in 1864 during the Wars of German Unification, the sisters
became the core of an anti-Prussian coalition that prefigured the great
anti-German alliance of 1914. Their sons, King George V and Tsar
Nicholas II were also close friends. The programme also looks at the
tangled relationship between the German Kaiser and his English mother,
Vicky – the oldest daughter of Queen Victoria. Disabled from birth,
Kaiser Wilhelm had a complex love/hate attitude towards Vicky, which
transferred itself to Britain as a whole, strongly influencing his
foreign policy
Now past the PBS of the cousins at war, consider here in the US during the same time:
Jacob Henry Schiff was a Jewish-American banker, businessman, and philanthropist. Among many other things, he helped finance the expansion of American railroads and the Japanese military efforts against Tsarist Russia in the Russo-Japanese War. In 1919, G.H. (Bert) Walker, a St. Louis-born, British-schooled operative of British and Morgan bankers, set up a private bank for E.H. Harriman’s sons, Averell and Roland, W.A. Harriman and Company. E.H. Harriman acquiring the bankrupt Union Pacific Railroad, financed through the British royal family’s private financier, Sir Ernst Cassel, Cassel’s New York partner Jacob Schiff, and members of the Rockefeller family. Like everything else on Wall Street, the financiers traded on what others had created. A banker and philanthropist, Jacob H. Schiff secured European funding to build America’s railroads, mines, and other enterprises. He helped transform the United States into the world’s leading industrialized economy.
A Russian Warship Was Discovered with an Estimated $130 Billion in Gold on Board
How did the Russo Japanese War impact Japan's modernization?
The Russo-Japanese War was a brief conflict but created significant problems for the tsarist regime. It was triggered by Nicholas II and his wish to expand the Russian empire in Asia. ... Even more telling was the economic impact the war had on the Russian economy, which fanned the flames of revolution in 1905.
Tsar Nicholas II's murder 100 years on: The terrible fate of Russia’s imperial family
In 1926, Bert brought his son-in-law, Prescott Bush, into this enterprise, Prescott and Roland Harriman having sworn lifetime blood oaths to each other as members of Yale’s secret satanic Skull and Bones society. Beginning in 1920, W.A. Harriman and Company under Bert Walker’s direction, began looting post-World War I Germany, acquiring control over shipping (the Hamburg-America ship line), and buying into steel production and raw materials. When the Depression hit, W.A. Harriman merged with Brown Brothers, the British family investment firm of Montagu Norman, the pro-Nazi head of the Bank of England. Brown Brothers Harriman was the largest private investment bank in the United States, and Prescott Bush was installed as its managing director. According to his account, Prescott presided over the weekly Thursday partners meeting at the firm, assisted by “silent and properly attired British floor attendants.”
Prescott Bush presided over a banking complex tightly interwoven with the funding centers for Adolf Hitler and the Nazi party. Most notable was their subsidiary, the Union Banking Corporation (UBC), a money-management front for Fritz Thyssen, the leading German steel and coal tycoon. Brown Brothers Harriman was also the bank of the Consolidated Silesian Steel Company, which included Thyssen’s Nazi business partner Friedrich Flick among its owners, and utilized slave labor from Auschwitz in its operations. In addition, Bush was the director of a number of companies associated with Thyssen, including the Silesian American Corporation. Thyssen, by his own account, was the chief financier of Hitler’s rise to power in Germany. By the late 1930s, Brown Brothers Harriman had bought and shipped millions of dollars of gold, fuel, steel, coal, and U.S. Treasury bonds to Germany, both feeding and financing Hitler’s war build-up.
Now past the PBS of the cousins at war, consider here in the US during the same time:
Jacob Henry Schiff was a Jewish-American banker, businessman, and philanthropist. Among many other things, he helped finance the expansion of American railroads and the Japanese military efforts against Tsarist Russia in the Russo-Japanese War. In 1919, G.H. (Bert) Walker, a St. Louis-born, British-schooled operative of British and Morgan bankers, set up a private bank for E.H. Harriman’s sons, Averell and Roland, W.A. Harriman and Company. E.H. Harriman acquiring the bankrupt Union Pacific Railroad, financed through the British royal family’s private financier, Sir Ernst Cassel, Cassel’s New York partner Jacob Schiff, and members of the Rockefeller family. Like everything else on Wall Street, the financiers traded on what others had created. A banker and philanthropist, Jacob H. Schiff secured European funding to build America’s railroads, mines, and other enterprises. He helped transform the United States into the world’s leading industrialized economy.
A Russian Warship Was Discovered with an Estimated $130 Billion in Gold on Board
How did the Russo Japanese War impact Japan's modernization?
The Russo-Japanese War was a brief conflict but created significant problems for the tsarist regime. It was triggered by Nicholas II and his wish to expand the Russian empire in Asia. ... Even more telling was the economic impact the war had on the Russian economy, which fanned the flames of revolution in 1905.
Tsar Nicholas II's murder 100 years on: The terrible fate of Russia’s imperial family
In 1926, Bert brought his son-in-law, Prescott Bush, into this enterprise, Prescott and Roland Harriman having sworn lifetime blood oaths to each other as members of Yale’s secret satanic Skull and Bones society. Beginning in 1920, W.A. Harriman and Company under Bert Walker’s direction, began looting post-World War I Germany, acquiring control over shipping (the Hamburg-America ship line), and buying into steel production and raw materials. When the Depression hit, W.A. Harriman merged with Brown Brothers, the British family investment firm of Montagu Norman, the pro-Nazi head of the Bank of England. Brown Brothers Harriman was the largest private investment bank in the United States, and Prescott Bush was installed as its managing director. According to his account, Prescott presided over the weekly Thursday partners meeting at the firm, assisted by “silent and properly attired British floor attendants.”
Prescott Bush presided over a banking complex tightly interwoven with the funding centers for Adolf Hitler and the Nazi party. Most notable was their subsidiary, the Union Banking Corporation (UBC), a money-management front for Fritz Thyssen, the leading German steel and coal tycoon. Brown Brothers Harriman was also the bank of the Consolidated Silesian Steel Company, which included Thyssen’s Nazi business partner Friedrich Flick among its owners, and utilized slave labor from Auschwitz in its operations. In addition, Bush was the director of a number of companies associated with Thyssen, including the Silesian American Corporation. Thyssen, by his own account, was the chief financier of Hitler’s rise to power in Germany. By the late 1930s, Brown Brothers Harriman had bought and shipped millions of dollars of gold, fuel, steel, coal, and U.S. Treasury bonds to Germany, both feeding and financing Hitler’s war build-up.
Richard Bowditch "Dick" Wigglesworth served as legal adviser to the Assistant Secretary of the Treasury in charge of foreign loans and railway payments, and secretary of the World War Debt Commission 1922-1924 and 1924: James Brown MP (made a privy counsellor before serving again in 1930)
barnstorm
Cicadas In Their Prime
Heisenberg honeycombs solve Veneziano puzzle
Heisenbug
In computer programming jargon, a heisenbug is a software bug that seems to disappear or alter its behavior when one attempts to study it.[1] The term is a pun on the name of Werner Heisenberg, the physicist who first asserted the observer effect of quantum mechanics, which states that the act of observing a system inevitably alters its state. In electronics the traditional term is probe effect, where attaching a test probe to a device changes its behavior.Similar terms, such as bohrbug, mandelbug,[2][3][4] hindenbug, and schrödinbug[5][6] (see the section on related terms) have been occasionally proposed for other kinds of unusual software bugs, sometimes in jest;[7][8] however, unlike the term heisenbug, they are not widely known or used
The absence of good (Latin: privatio boni) is a theological doctrine that evil, unlike good, is insubstantial, so that thinking of it as an entity is misleading. Instead, evil is rather the absence or lack ("privation") of good.
Watch: Why Do Cicadas Only Show Up at Prime Intervals of 13 And 17 Years?
15 Foods For Good Gut Health
| Biology | Microbiology |
How the Western Diet Has Derailed Our Evolution
Burgers and fries have nearly killed our ancestral microbiome.
By Moises Velasquez-Manoff
Illustration by Katherine Diemert
November 12, 2015
CLU (programming language)
CLU is a programming language created at the Massachusetts Institute of Technology (MIT) by Barbara Liskov
and her students between 1974 and 1975. While it did not find extensive
use, it introduced many features that are used widely now, and is seen
as a step in the development of object-oriented programming (OOP).
The Architect of Modern Algorithms
Barbara
Liskov pioneered the modern approach to writing code. She warns that
the challenges facing computer science today can’t be overcome with good
design alone.
While the name “Stigler Diet” was applied after the experiment by outsiders, according to Stigler, “No one recommends these diets for anyone, let alone everyone.” The Stigler diet has been much ridiculed for its lack of variety and palatability; however, his methodology has received praise and is considered to be some of the earliest work in linear programming.
A Bézier curve (/ˈbɛz.i.eɪ/ BEH-zee-ay)[1] is a parametric curve used in computer graphics and related fields.[2] The curve, which is related to the Bernstein polynomial, is named after Pierre Bézier, who used it in the 1960s for designing curves for the bodywork of Renault cars.[3] Other uses include the design of computer fonts and animation.[3] Bézier curves can be combined to form a Bézier spline, or generalized to higher dimensions to form Bézier surfaces.[3] The Bézier triangle is a special case of the latter.
Stigler diet
The Stigler diet is an optimization problem named for George Stigler, a 1982 Nobel Laureate in economics, who posed the following problem:For a moderately active man weighing 154 pounds, how much of each of 77 foods should be eaten on a daily basis so that the man’s intake of nine nutrients will be at least equal to the recommended dietary allowances (RDAs) suggested by the National Research Council in 1943, with the cost of the diet being minimal?The nutrient RDAs required to be met in Stigler’s experiment were calories, protein, calcium, iron, as well as vitamins A, B1, B2, B3, and C. The result was an annual budget allocated to foods such as evaporated milk, cabbage, dried navy beans, and beef liver at a cost of approximately $0.11 a day in 1939 U.S. dollars.
While the name “Stigler Diet” was applied after the experiment by outsiders, according to Stigler, “No one recommends these diets for anyone, let alone everyone.” The Stigler diet has been much ridiculed for its lack of variety and palatability; however, his methodology has received praise and is considered to be some of the earliest work in linear programming.
The Diet Problem
Summary: The goal of the diet problem
is to select a set of foods that will satisfy a set of daily
nutritional requirement at minimum cost. The problem is formulated as a
linear program where the objective is to minimize cost and the
constraints are to satisfy the specified nutritional requirements. The
diet problem constraints typically regulate the number of calories and
the amount of vitamins, minerals, fats, sodium, and cholesterol in the
diet. While the mathematical formulation is simple, the solution may
not be palatable!
Mathematical Programming
Diet Problem
Diet Problem in Linear Programming solved with Excel Solver
Polyhedral techniques in combinatorial optimization
In computer science, an enumeration algorithm is an algorithm that enumerates the answers to a computational problem.
A checksum is a small-sized datum derived from a block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage.
It is usually applied to an installation file after it is received
from the download server. By themselves, checksums are often used to
verify data integrity but are not relied upon to verify data authenticity.
The rank-nullity theorem is a fundamental theorem in linear
algebra which relates the dimensions of a linear map's kernel and image
with the dimension of its domain.
In linear algebra, the Cayley–Hamilton theorem (named after the mathematicians Arthur Cayley and William Rowan Hamilton) states that every square matrix over a commutative ring (such as the real or complex field) satisfies its own characteristic equation.
Physiocracy (French: Physiocratie; from the Greek for "government of nature") is an economic theory
developed by a group of 18th-century Enlightenment French economists
who believed that the wealth of nations was derived solely from the
value of "land agriculture" or "land development" and that agricultural products should be highly priced. Their theories originated in France and were most popular during the second half of the 18th century. Physiocracy is one of the first well-developed theories of economics.
The movement was particularly dominated by François Quesnay (1694–1774) and Anne-Robert-Jacques Turgot (1727–1781). It immediately preceded the first modern school, classical economics, which began with the publication of Adam Smith's The Wealth of Nations in 1776.
The movement was particularly dominated by François Quesnay (1694–1774) and Anne-Robert-Jacques Turgot (1727–1781). It immediately preceded the first modern school, classical economics, which began with the publication of Adam Smith's The Wealth of Nations in 1776.
Here’s Who Owns the Most Land in America
The 100 largest private landowners in the U.S. own 40 million acres—an area the size of Florida.
John Law and the Mississippi Bubble: 1718-1720
The first map of America’s food supply chain is mind-boggling
Most of our food is moved across great distances—and through many different forms of transit—before it reaches our plates.
Physicists Have Finally Seen Traces of a Long-Sought Particle (Axion). Here's Why That's a Big Deal.
Magnetic space group, Graphene reinforced CSA Cement, minimum-cost flow problem (MCFP)U.S. patent board is unconstitutional, but problem can be fixed: appeals court
The Simplex Algorithm
The simplex algorithm is the classical method to solve the optimization problem of linear programming.Dual linear program
The dual of a given linear program (LP) is another LP that is derived from the original (the primal) LP in the following schematic way
In dance, a pivot turn (or simply pivot) is a general classification for dance turns in which the performer's body rotates about its vertical axis without traveling.
A Native American pivot turn, as described by Bessie and May Evans (1931), is performed standing on the ball of one foot and tapping with the other foot, accompanied with small turns on the standing foot with each tap. The full turn requires about 16 taps.
A Russian pivot turn, as described by Bessie and May Evans, is performed as follows. The right foot is placed flat and the left foot is placed with the toe by the right heel and the left heel raised and this relative position basically maintained during the turning. The turn starts with the right foot raised from the floor. While continuously revolving, on each strong beat (downbeat) the right foot is stepped flat and on each weak beat (upbeat) the left foot is stepped on the ball (by the right heel).
A Native American pivot turn, as described by Bessie and May Evans (1931), is performed standing on the ball of one foot and tapping with the other foot, accompanied with small turns on the standing foot with each tap. The full turn requires about 16 taps.
A Russian pivot turn, as described by Bessie and May Evans, is performed as follows. The right foot is placed flat and the left foot is placed with the toe by the right heel and the left heel raised and this relative position basically maintained during the turning. The turn starts with the right foot raised from the floor. While continuously revolving, on each strong beat (downbeat) the right foot is stepped flat and on each weak beat (upbeat) the left foot is stepped on the ball (by the right heel).
The Simplex Method: pivoting to find the optimum Simplex tableau
Lemke–Howson algorithm
The Lemke–Howson algorithm
is an algorithm that computes a
Nash equilibrium of a bimatrix game, named after its inventors, Carlton E. Lemke and J. T. Howson.
It is said to be “the best known among the combinatorial algorithms for finding a Nash equilibrium”
In game theory and economic theory, a zero-sum game is a mathematical representation of a situation in which each participant's gain or loss of utility
is exactly balanced by the losses or gains of the utility of the other
participants. If the total gains of the participants are added up and
the total losses are subtracted, they will sum to zero.
Definition - What does Training Data mean?
The idea of using training data in machine learning programs
is a simple concept, but it is also very foundational to the way that
these technologies work. The training data is an initial set of data
used to help a program understand how to apply technologies like neural
networks to learn and produce sophisticated results. It may be
complemented by subsequent sets of data called validation and testing
sets.
Training data is also known as a training set, training dataset or learning set.
Training data is also known as a training set, training dataset or learning set.
In machine learning, a common task is the study and construction of algorithms that can learn from and make predictions on data. Such algorithms work by making data-driven predictions or decisions, through building a mathematical model from input data.
The data used to build the final model usually comes from multiple datasets. In particular, three data sets are commonly used in different stages of the creation of the model.
The data used to build the final model usually comes from multiple datasets. In particular, three data sets are commonly used in different stages of the creation of the model.
Definition - What does Learning Algorithm mean?
A learning algorithm is an algorithm
used in machine learning to help the technology to imitate the human
learning process. Combined with technologies like neural networks, learning algorithms create involved, sophisticated learning programs.
Commonly used Machine Learning Algorithms (with Python and R Codes)
Supervised learning is the machine learning task of learning a function that maps an input to an output based on example input-output pairs.[1] It infers a function from labeled training data consisting of a set of training examples.[2] In supervised learning, each example is a pair consisting of an input object (typically a vector) and a desired output value (also called the supervisory signal). A supervised learning algorithm analyzes the training data and produces an inferred function, which can be used for mapping new examples. An optimal scenario will allow for the algorithm to correctly determine the class labels for unseen instances. This requires the learning algorithm to generalize from the training data to unseen situations in a "reasonable" way (see inductive bias).
The parallel task in human and animal psychology is often referred to as concept learning.
What Is The Nonnegativity Constraint?
Learn more about Nonnegativity
Compressed sensing
Compressed sensing (also known as compressive sensing, compressive sampling, or sparse sampling) is a signal processing technique for efficiently acquiring and reconstructing a signal, by finding solutions to underdetermined linear systems.
This is based on the principle that, through optimization, the sparsity
of a signal can be exploited to recover it from far fewer samples than
required by the Nyquist–Shannon sampling theorem. There are two conditions under which recovery is possible.[1] The first one is sparsity, which requires the signal to be sparse in some domain. The second one is incoherence, which is applied through the isometric property, which is sufficient for sparse signals
[A look at how CS can improve on current imaging techniques]
In the mathematical fields of geometry and linear algebra, a principal axis is a certain line in a Euclidean space associated with an ellipsoid or hyperboloid, generalizing the major and minor axes of an ellipse or hyperbola. The principal axis theorem states that the principal axes are perpendicular, and gives a constructive procedure for finding them.
Mathematically, the principal axis theorem is a generalization of the method of completing the square from elementary algebra. In linear algebra and functional analysis, the principal axis theorem is a geometrical counterpart of the spectral theorem. It has applications to the statistics of principal components analysis and the singular value decomposition. In physics, the theorem is fundamental to the study of angular momentum.
Mathematically, the principal axis theorem is a generalization of the method of completing the square from elementary algebra. In linear algebra and functional analysis, the principal axis theorem is a geometrical counterpart of the spectral theorem. It has applications to the statistics of principal components analysis and the singular value decomposition. In physics, the theorem is fundamental to the study of angular momentum.
Goppa code
In mathematics, an algebraic geometric code (AG-code), otherwise known as a Goppa code, is a general type of linear code constructed by using an algebraic curve  over a finite field
over a finite field  . Such codes were introduced by Valerii Denisovich Goppa. In particular cases, they can have interesting extremal properties. They should not be confused with binary Goppa codes that are used, for instance, in the McEliece cryptosystem.
. Such codes were introduced by Valerii Denisovich Goppa. In particular cases, they can have interesting extremal properties. They should not be confused with binary Goppa codes that are used, for instance, in the McEliece cryptosystem.
 over a finite field
over a finite field  . Such codes were introduced by Valerii Denisovich Goppa. In particular cases, they can have interesting extremal properties. They should not be confused with binary Goppa codes that are used, for instance, in the McEliece cryptosystem.
. Such codes were introduced by Valerii Denisovich Goppa. In particular cases, they can have interesting extremal properties. They should not be confused with binary Goppa codes that are used, for instance, in the McEliece cryptosystem.
In coding theory, a cyclic code is a block code, where the circular shifts of each codeword gives another word that belongs to the code. They are error-correcting codes that have algebraic properties that are convenient for efficient error detection and correction.
when in danger or in doubt, run in circles scream and shout (then go take a nap)
Overwhelming feelings of anxiety and frantic agitation are consistent with an animalistic fight-or-flight reaction for considerations
epinephrine (adrenaline) is a stress hormone that is released by the adrenal system...
In the brain, dopamine functions as a neurotransmitter—a chemical released by neurons (nerve cells) to send signals to other nerve cells
Schlumberger Geophones
In 1978, Bush and Osama bin Laden's brother, Salem bin Laden, founded Arbusto Energy, an oil company based in Texas.
By George Lardner Jr. and Lois Romano
Washington Post Staff Writers
Friday, July 30, 1999
Solar v Coal, Montreux Convention, Crude Tanker War trader with Bridges transition Smale's solutions
By David V. B. HirschReplicates and repeats—what is the difference and is it significant?
A brief discussion of statistics and experimental designWashington Post Staff Writers
Friday, July 30, 1999



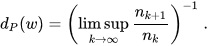














Comments
Post a Comment